Create a Classic Key
Classic keys can either be generated by Akeyless, or imported into the Akeyless KMS from another source. Akeyless supports both AES-256-GCM and RSA 2048 keys.
NoteIf you are going to share the classic key with a Cloud KMS, you need to create a target for the Cloud KMS. You can then either specify this target when you create the key, or associate the key with the target at a later date.
You can create a classic key using the Akeyless CLI. If you’d prefer, see how to do this from the Akeyless Gateway instead.
Create a Classic Key with the CLI
The syntax to create a classic key is:
akeyless create-classic-key /
--name <classic key name> /
--alg <AES256GCM|RSA2048> /
--target-name <target name>Where:
- name: The name of the classic key. The name can include the path to the virtual folder in which you want to create the new key, using slash
/separators. If the folder does not exist, it will be created together with the key. - alg: The type of key to be created, either
AES256GCMorRSA2048. - target-name: The name of the target with which to share the key. This value is optional. If you do not share the key with a Cloud KMS when you create it, you can do so at a later date, as described in Associate a Classic Key and a Target.
The full list of options for this command is:
-n, --name *Classic key name
-a, --alg *Key type; options: [AES256GCM, RSA2048]
---p, ----key-file-path Path to file with the classic key value provided by user
----key-data Base64-encoded classic key value provided by user
-m, --metadata Metadata about the classic key
-t, --tag List of the tags attached to this secret. To specify multiple tags use argument multiple times: -t Tag1 -t Tag2
-k, --key The name of the key that protects the classic key value (if empty, the account default key will be used)
--target-name The target name to associate with this classic key
--profile Use a specific profile from your akeyless/profiles/ folder
--username Optional username for various authentication flows
--password Optional password for various authentication flows
--uid-token The universal identity token, Required only for universal_identity authentication
-h, --help display help information
--json[=false] Set output format to JSON
--no-creds-cleanup[=false] Do not clean local temporary expired credentialsCreate a Classic Key from the Akeyless Gateway
You can create a classic key using the Akeyless Gateway. If you’d prefer, see how to do this from the Akeyless CLI instead.
-
In the Akeyless Gateway UI, select Classic Keys > New.
-
Define the following:
- Name: The name of the classic key.
- Location: The path to the virtual folder in which you want to create the new key, using slash
/separators. If the folder does not exist, it will be created together with the key. - Description: An optional description of the key.
- Key Type: The type of key to be created, either
AES256GCMorRSA2048. - Target: The name of the target with which to share the key. This value is optional. If you do not share the key with a Cloud KMS when you create it, you can do so at a later date, as described in Associate a Classic Key and a Target.
- Generated By: Determines if the classic key should be generated by the Akeyless KMS, or uploaded from another source. If you select Import Classic Key, specify the path from which to upload the key.
- Encrypt with the following Key: The encryption key with which to encrypt the classic key (if your system includes multiple encryption keys). Otherwise, select
Default. - Auto Rotate: Indicate if the classic key should be automatically rotated. If you do not enable automatic rotation, you can rotate the key manually.
-
Select Save.
Shared Keys on a Cloud KMS
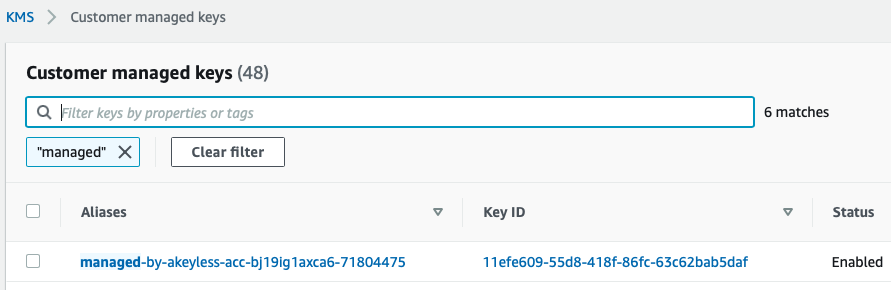
If you share a classic key with a Cloud KMS, you will find a new customer-managed key. The key alias is built as managed-by-<account-id>-<item-id>, as shown in the following example:
Updated 9 days ago
