TeamCity Plugin
When performing integration tests and deployments, build scripts need credentials to access external servers and services. The TeamCity plugin allows connecting TeamCity to the Akeyless Platform, requesting new credentials when a build starts, passing them to the build script, and revoking them immediately when it finishes.
Note:Akeyless developed API compatibility with HashiCorp Vault OSS, enabling the use of Vault OSS community plugins for both Static and Dynamic Secrets, you can find more information here
Prerequisites
-
A TeamCity server with an authorized BuildAgent.
-
An Authentication Methods configured in the Akeyless Platform with access to secrets that will be used by the build agent.
Info:Currently, TeamCity plugin supports three authentication methods:
Ensure that your Authentication Methods is associated with an access role that has sufficient permissions to access the required secrets.
Configure The TeamCity Plugin
-
Log in to TeamCity and go to Administration > Plugins.
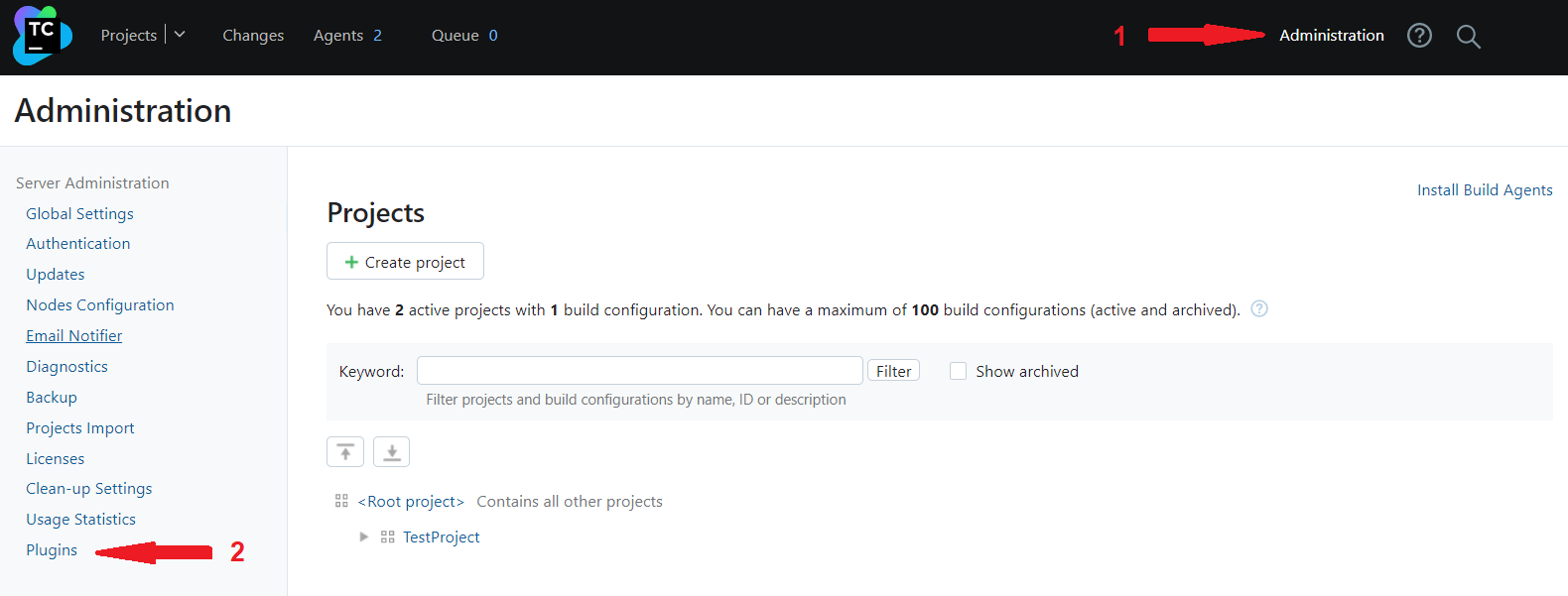
-
Click Browse plugins repository to find and download the
HashiCorp Vaultplugin.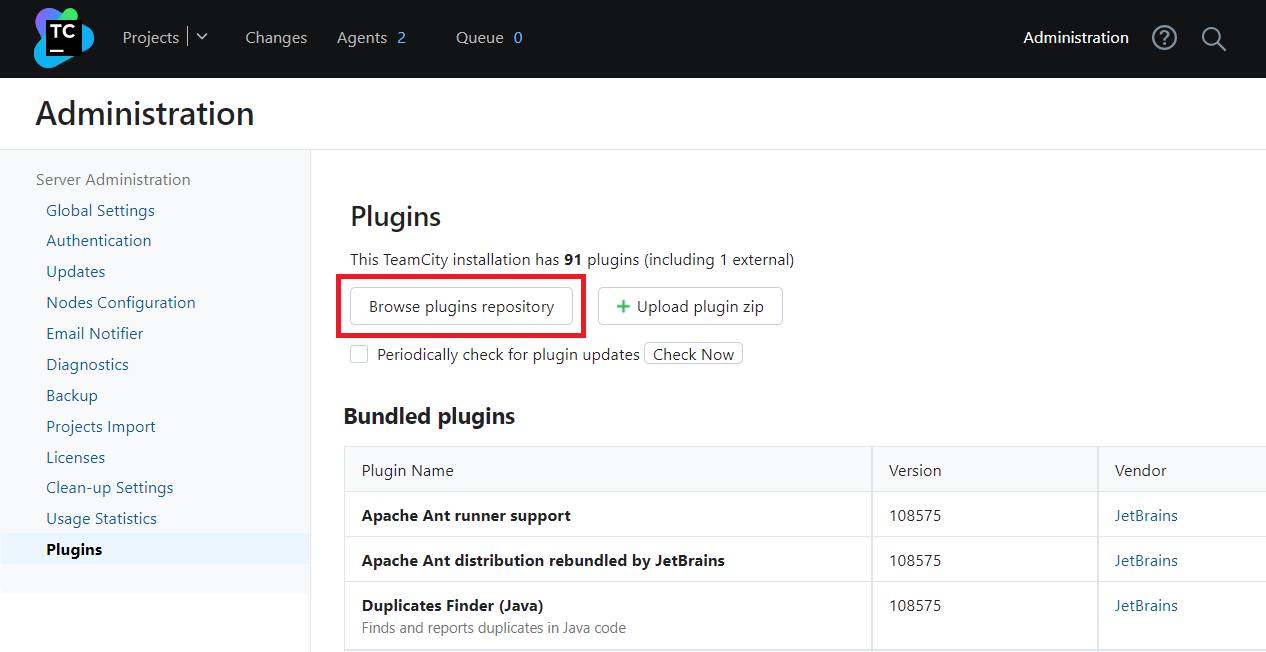
-
Then click Upload plugin ZIP to install the
Hashicorp Vaultplugin.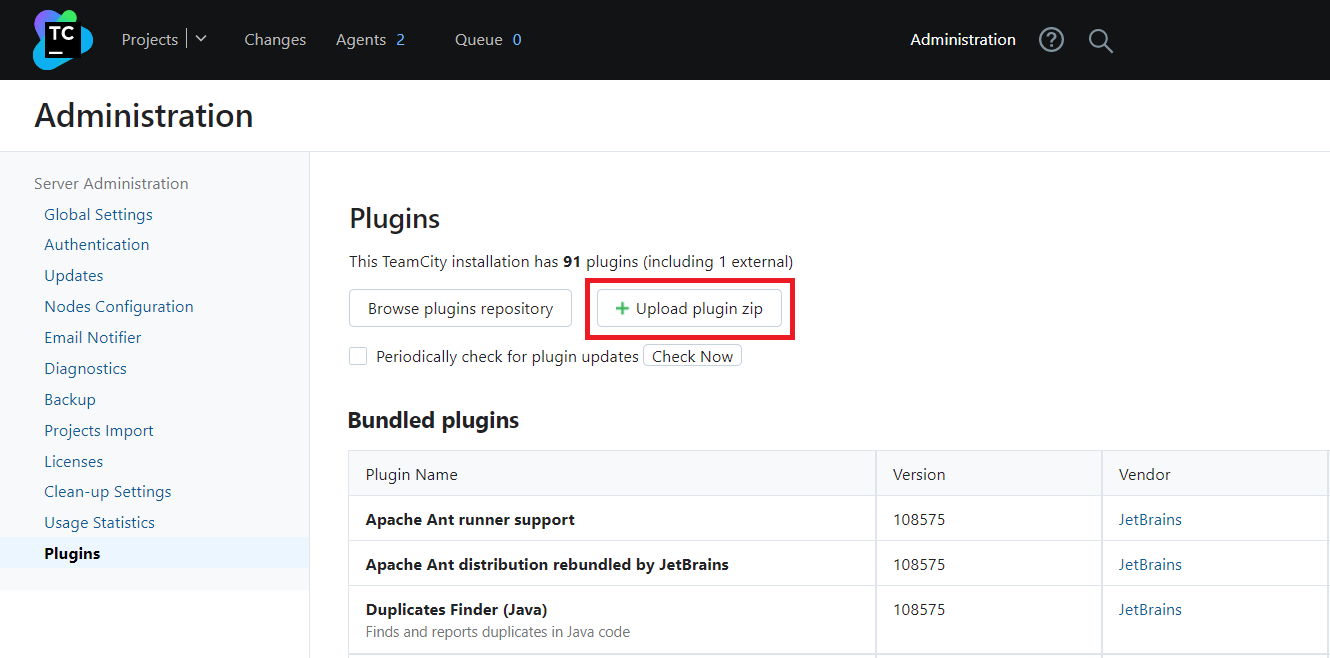
-
Go to Administration > Projects and create a new project.
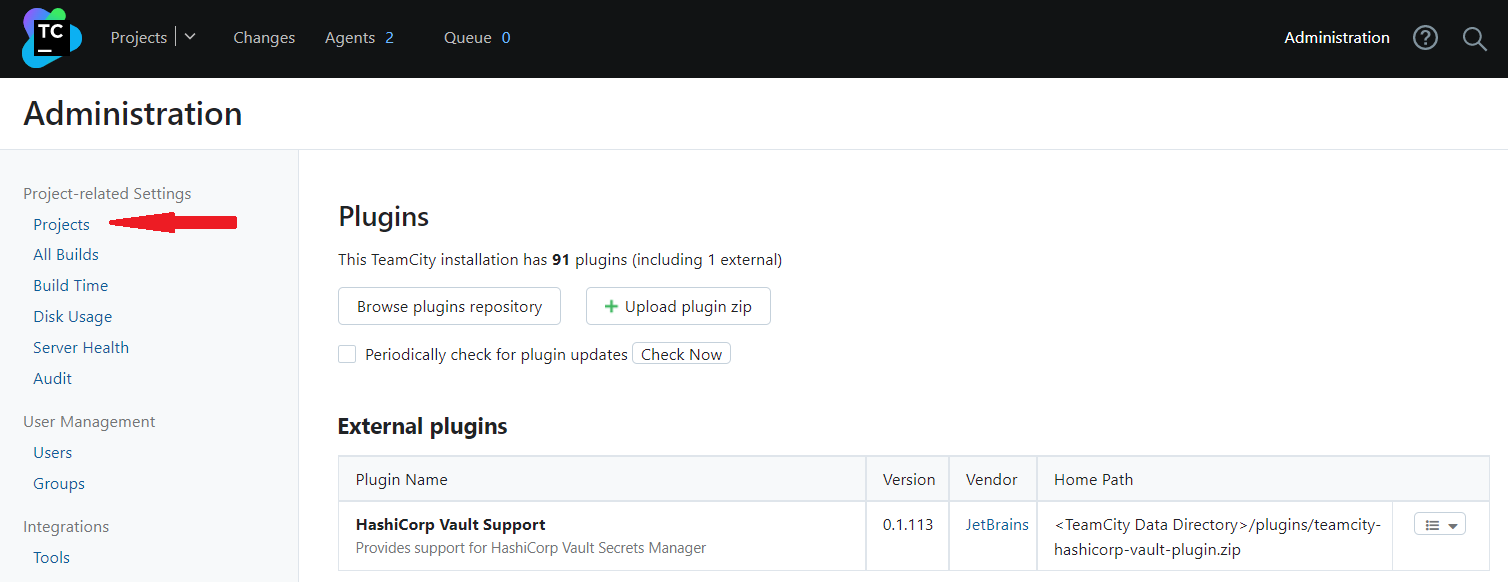
-
Open the created project and go to the Connections section.
-
Click Add Connection to connect your project to the
Vaultplugin.
-
Provide connection parameters to the Akeyless Platform in the pop-up window.
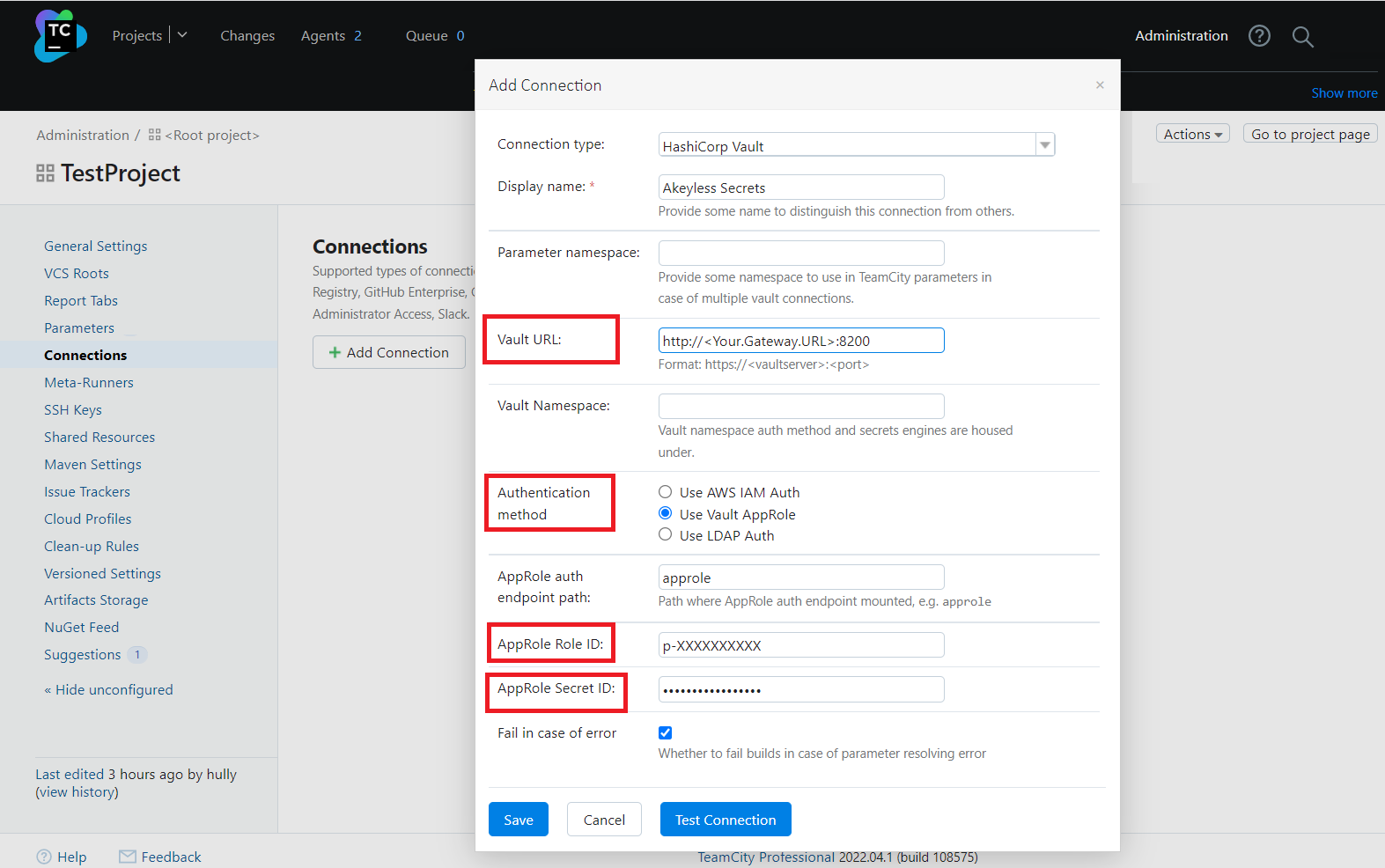
Where:
-
Vault URL: Specify your Gateway URL with the HashiCorp Vault Proxy port:
https://<Your-Gateway-URL>:8200or use the public endpoint of Akeyless HashiCorp Vault Proxy:https://hvp.akeyless.io. -
Authentication method: Select the authentication method to use when authenticating with Akeyless.
Available options: AWS IAM, LDAP, or Akeyless API Key (HashiCorp Vault AppRole).
For example, to use API Key set the following:
-
AppRole Role ID: Your API Key
Access ID. -
AppRole Secret ID:
Access Keyof the providedAccess ID.
Static Secrets
Let's create a static secret first. For that, run the following command:
akeyless create-secret --name hvp/test --value '{"password":"1234","username":"abcd"}'After that, you need to create an environment variable in your TeamCity project that will be used by build scripts to fetch a secret.
-
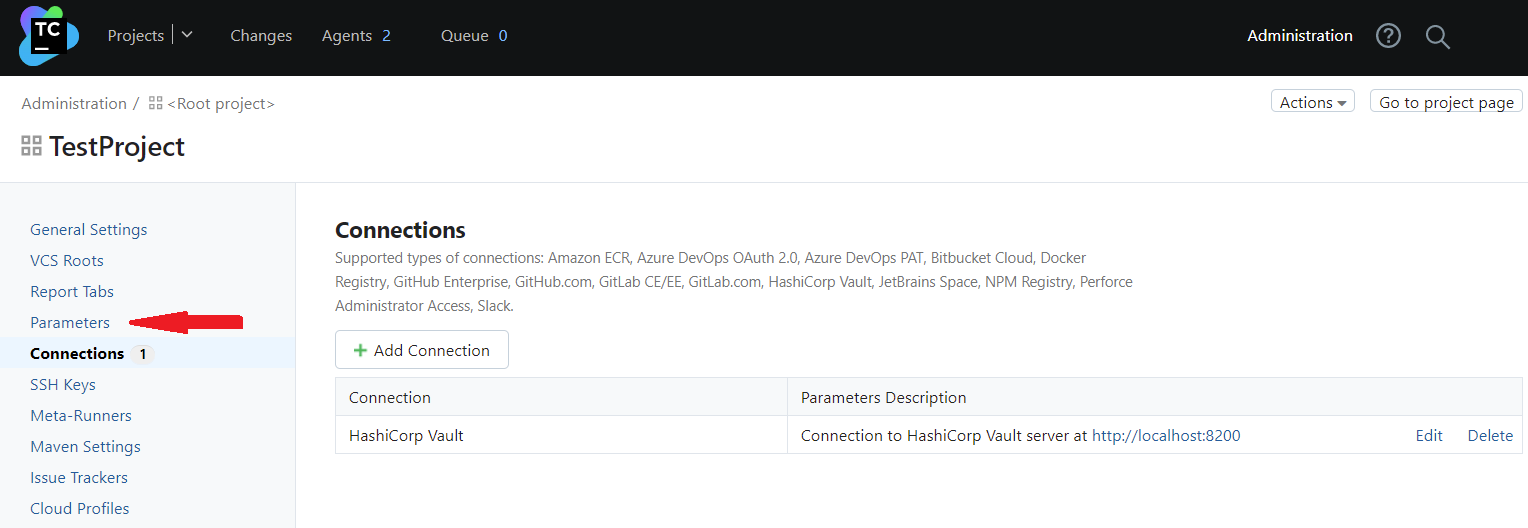
Go to the Parameters section to declare a new build parameter which will refer to the Akeyless secret. Currently, these values can be used in the build parameter declaration only and cannot be specified in build steps.
-
Click Add new parameter and provide the settings in the pop-up window.
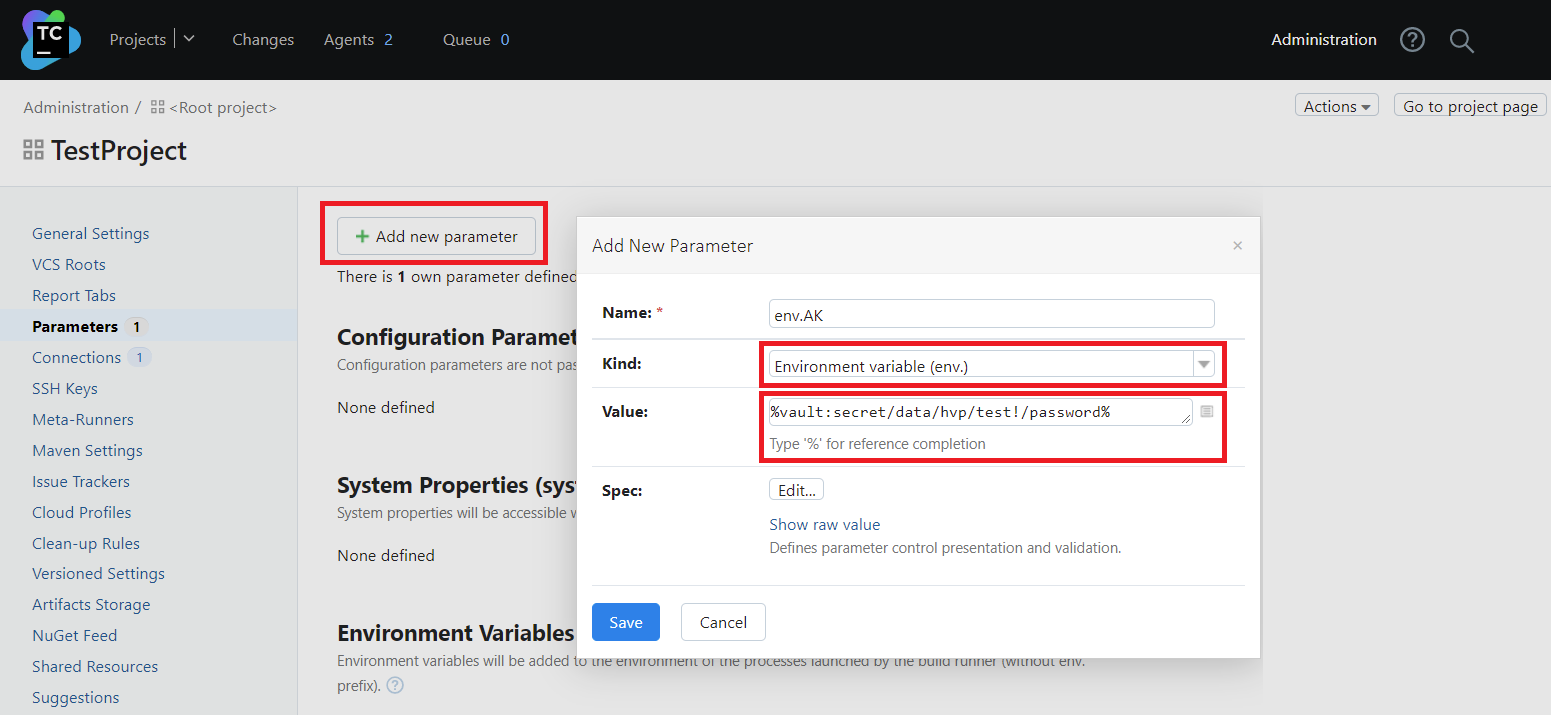
Where:
-
Name: Specify your parameter name (without any prefixes).
-
Kind: Select the Environment variable (env.) parameter type. This will add an env. prefix to the parameter name, but later in the build script, you should specify the name without a prefix.
-
Value: Provide the full path to your secret in Akeyless using the following format:
Syntax:
%vault:secret/PATH!KEY% where PATH is the secret full name, and KEY is the specific value inside.
In our example: %vault:secret/hvp/test!/password%
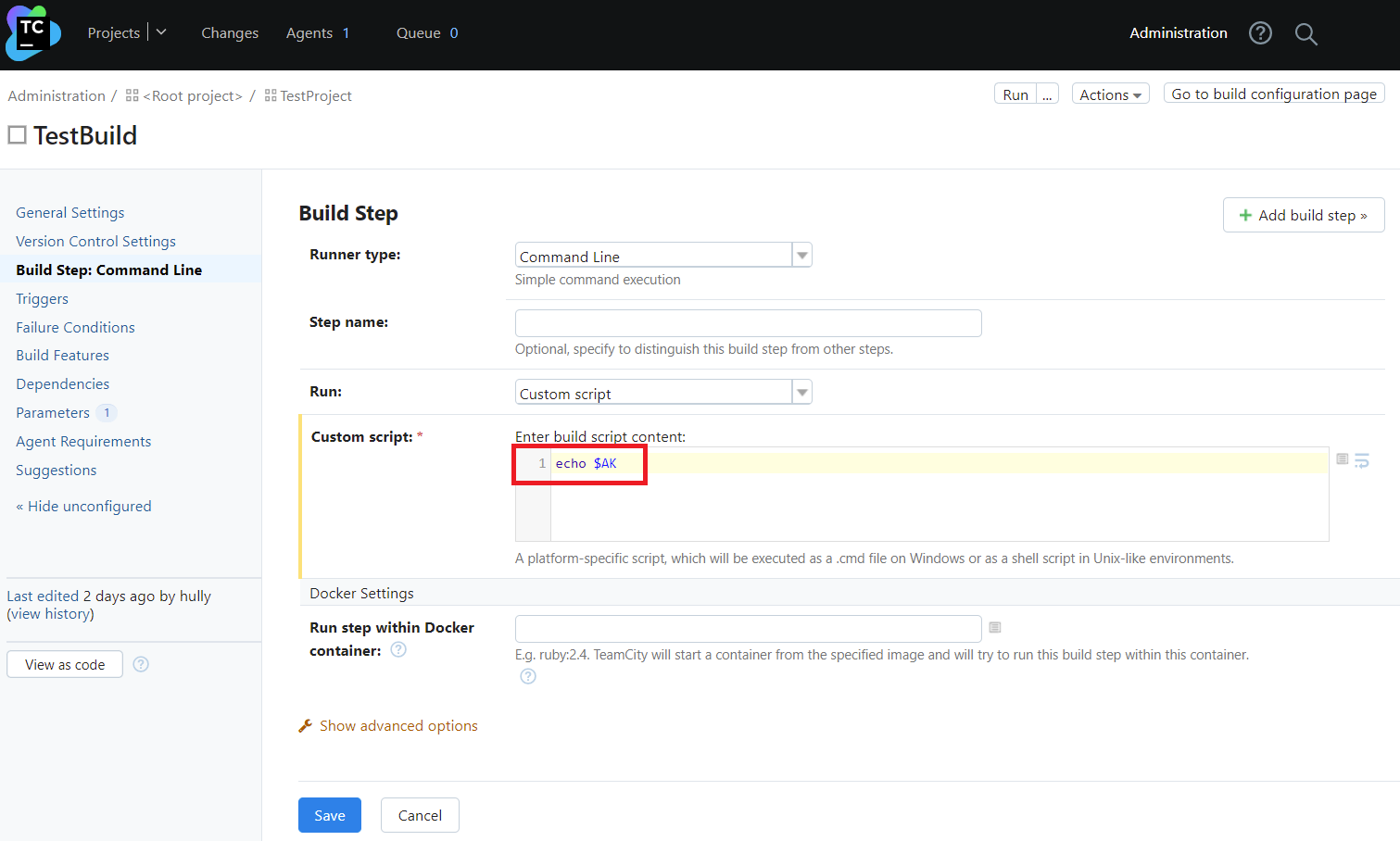
Finally, let's create a simple build script using this environment variable and run it:
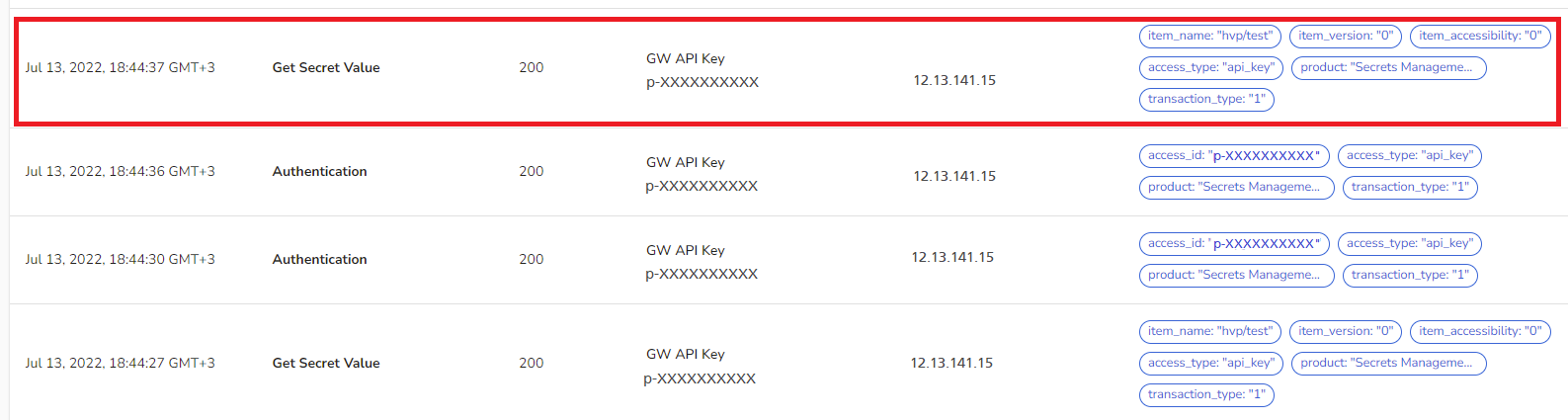
In the Audit Logs screen, you'll see that the script requested and successfully received the hvp/test secret value:
Dynamic Secrets
-
Go to the Parameters section to declare new build parameters for username and password which will refer to the corresponding dynamic secret values.
-
Click Add new parameter and provide the settings in the pop-up window.
Where:
-
Name: Specify your parameter name (without any prefixes).
-
Kind: Select the Environment variable (env.) parameter type. This will add an env. prefix to the parameter name, but later in the build script, you should specify the name without a prefix.
-
Value: Provide the full path to your secret in Akeyless using the following format:
Syntax:
%vault:/<dynamic-secret-type>/creds/<path/to/secretname>!/<JSON Entry>%
In our example: %vault:/mysql/creds/hvp/mysql!/username% and %vault:/mysql/creds/hvp/mysql!/password% where the dynamic secret name is /mysql.
Another example:
%vault:azure/creds/<path/to/secretname>!/user.password%
%vault:azure/creds/<path/to/secretname>!/user.userPrincipalName%
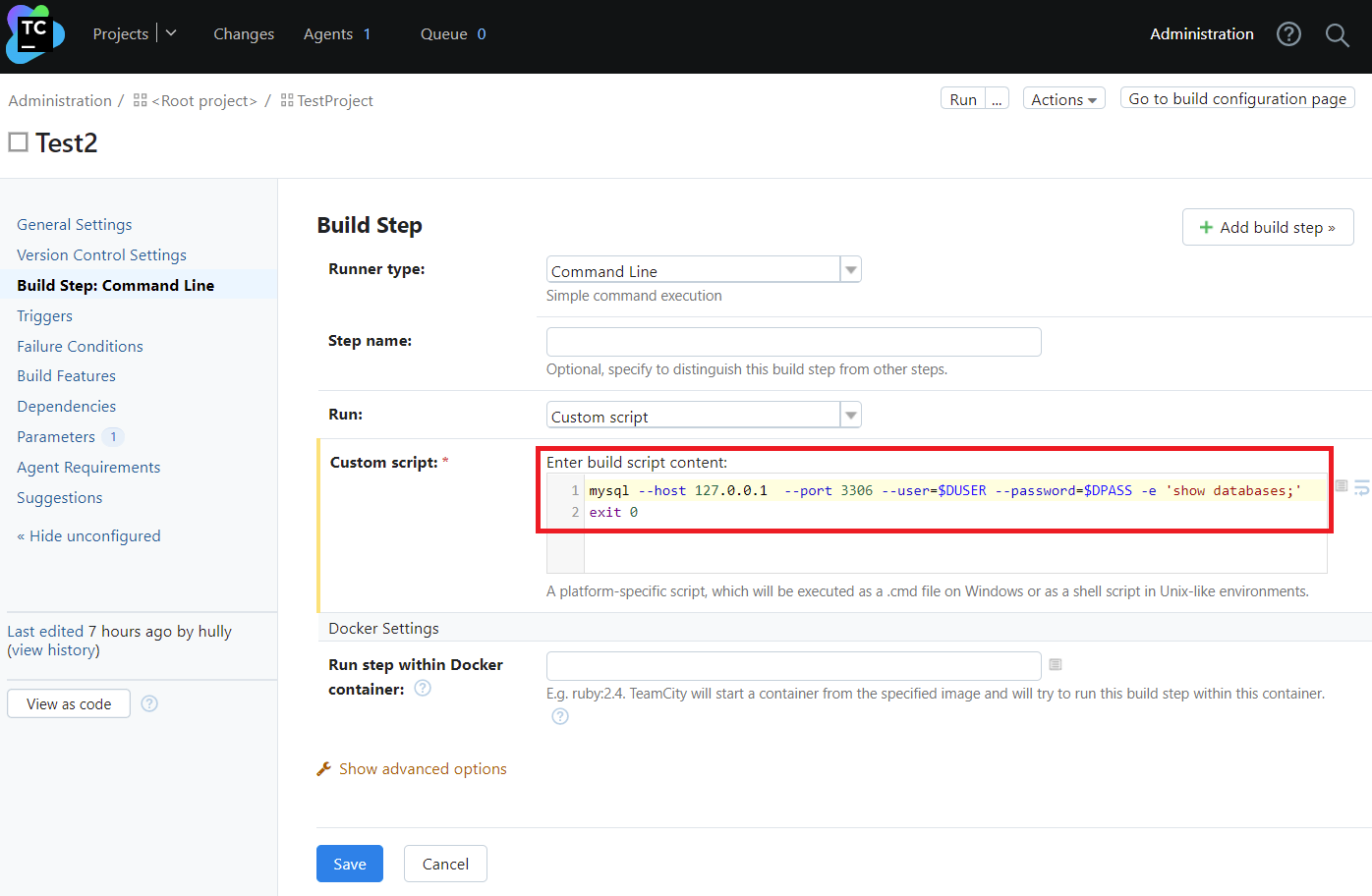
Finally, create a simple build script using this environment variable, and run it:
Updated 7 days ago
