Okta SAML Authentication
To use Okta as an IdP to authenticate to the Akeyless Platform, follow the steps below.
Create an Okta Application
The following configuration will enable users to authenticate using Okta SAML-based Single Sign-On.
-
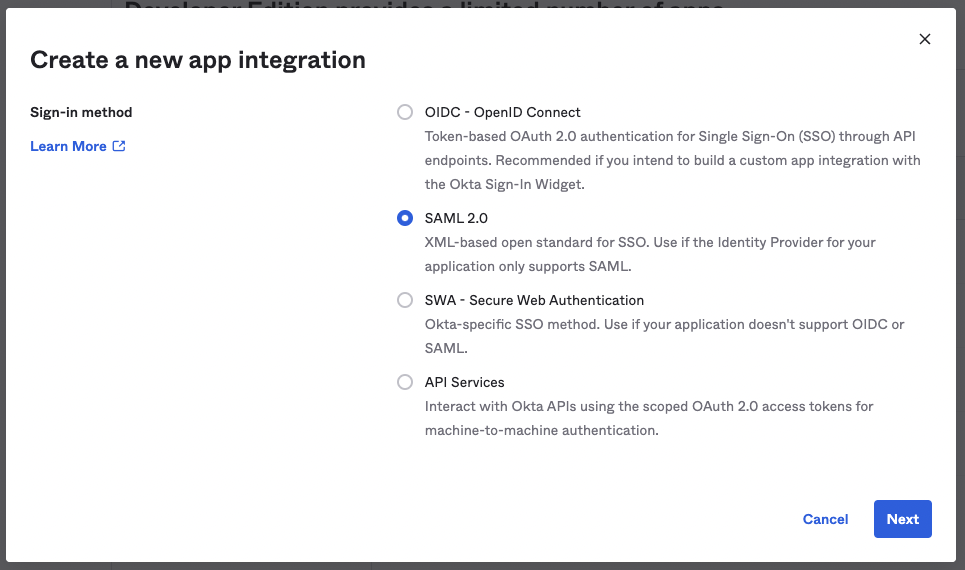
Go to Applications in the left sidebar. Create a new app integration type SAML 2.0 in your Okta account.
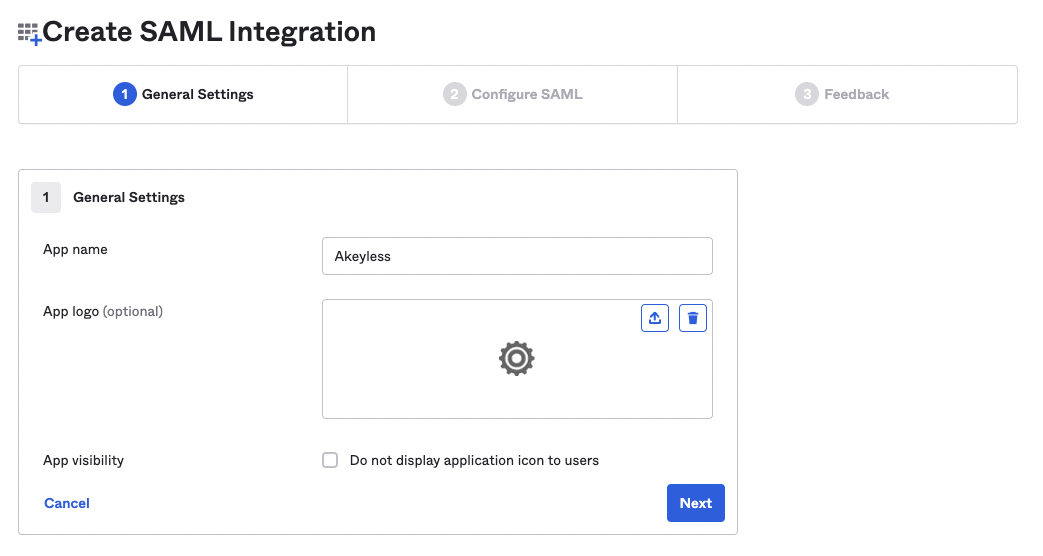
Provide an App name:
-
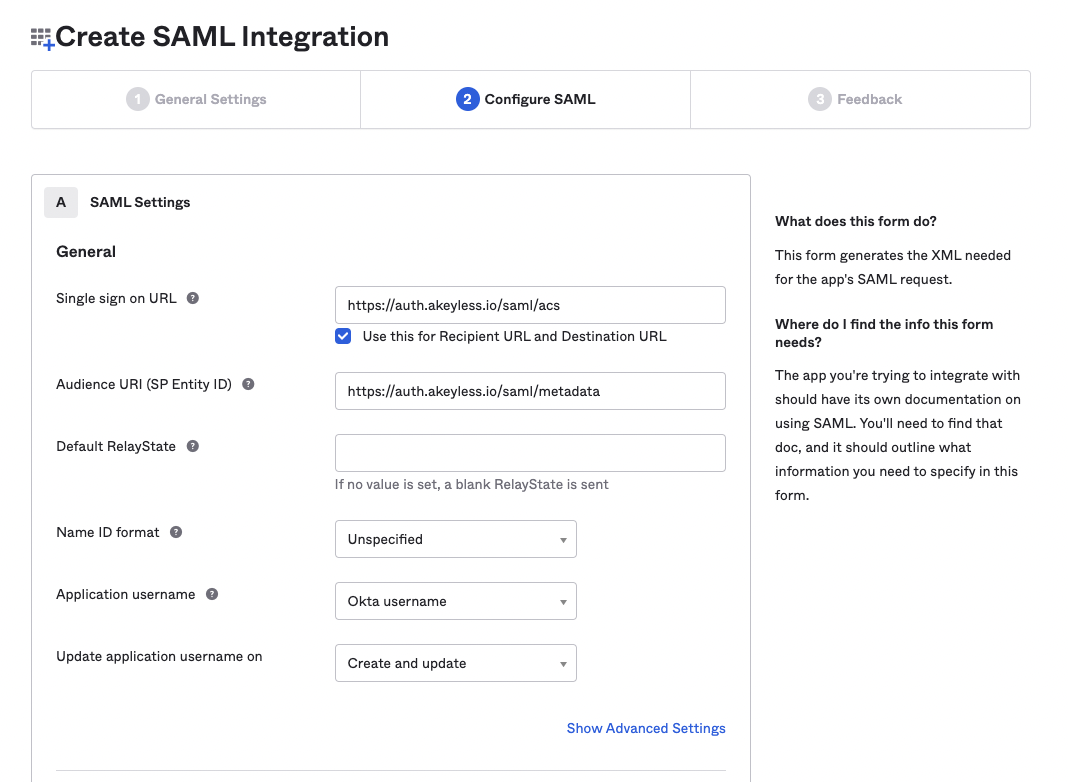
On the SAML Settings page:
- Set
https://auth.akeyless.io/saml/acsinto the Single sign-on URL field.- Set
https://auth.akeyless.io/saml/metadatainto the Audience URI (SP Entity ID) field.
- Set
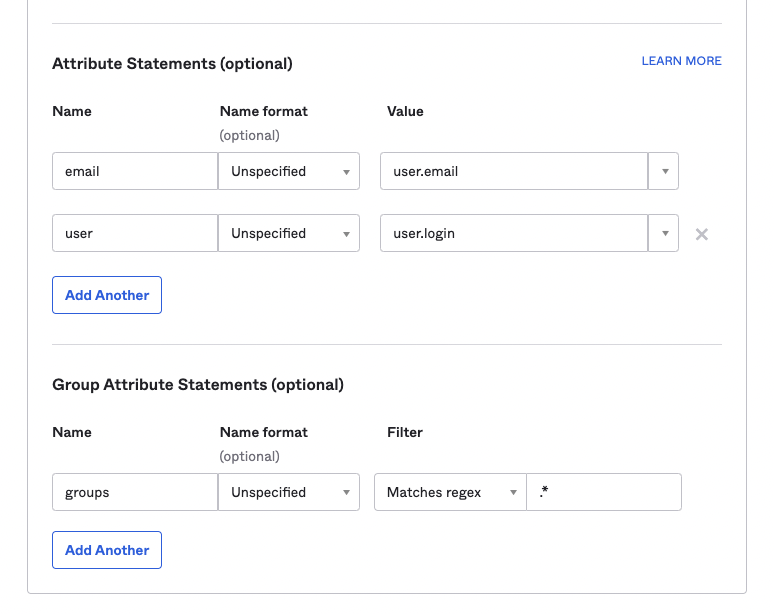
- In the Attribute Statements section, add the following attributes:
Name:email->Value:user.emailName:user->Value:user.login
- In the Group Attributes Statements section, add the following attributes:
Name:groupsFilter:Matches regex->Value:.*
- Set
-
On the Feedback page, click Finish.
-
You can either obtain your IdP Metadata URL by clicking on the Actions menu of the Active SAML Signing Certificate and copy the URL from the View IdP Metadata button. Alternatively, you can obtain the IdP metadata
XMLby clicking on View SAML setup instructions, and in the new tab that opens, scroll down and copy the full IdP metadataXMLunder the Optional section.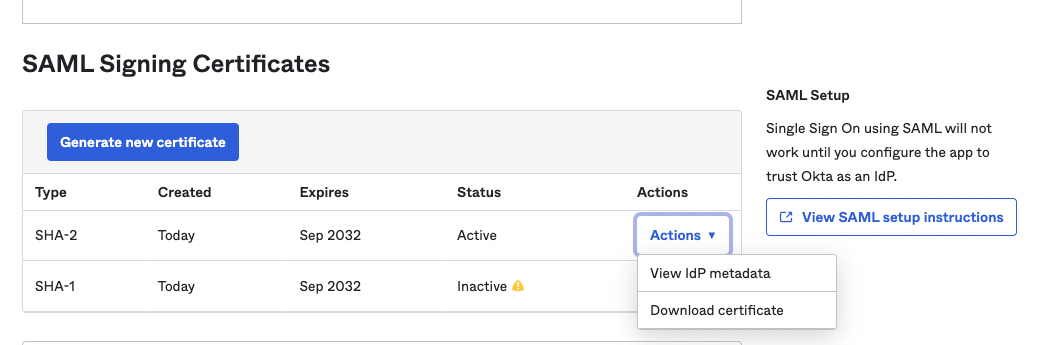
-
Now, when an Okta Application is ready, assign users to the Okta app, just like with any other Okta app.
-
To bind the Okta application with your Akeyless account, you need to create a SAML Authentication Method using either CLI or UI, as described below.
Create SAML Authentication Method
To create a SAML Auth Method using the Akeyless CLI run the following command:
akeyless auth-method create saml \
--name 'my Okta app' \
--idp-metadata-url '<your-idp-metadata-url>' \
--unique-identifier emailAlternatively, you can create this Auth Method from the Akeyless Console.
-
Go to the Users & Auth Methods tab in your console.
-
Select New > SAML.
-
Fill in the mandatory parameters:
- Name: The in-system name for the authentication method.
- IdP Metadata URL: The App Federation Metadata URL you copied from the Azure process.
- Unique identifier: The required identifier. In this case, you can use email.
Authenticate Using SAML
To log in using SAML from Akeyless CLI:
-
Configure a new profile with your Access ID from the previous step and SAML type (if no profile name is provided, the default will be configured):
akeyless configure --access-id <Access ID> --access-type saml --profile 'okta-app' -
Now, you can run any Akeyless CLI command and be authenticated with the Okta application:
akeyless list-items --profile okta-app
In the Akeyless Console login page, click the SAML option and enter your SAML Access ID. You will be redirected to the Okta sign-in page where you need to provide your Okta credentials.
Updated 10 days ago
