Rotated Secrets
Rotated Secrets enable you to protect the credentials for privileged-user accounts such as an Administrator account on a Windows Server, a root account on a Linux server, or an Admin account on a network device, by resetting its password.
Setting up Rotated Secrets requires the Rotated Secret permission on the Gateway. You can also set the Rotate Secret Value permission to allow rotation of the secret value without granting edit rights (this also requires Read permission on the rotated secret item).
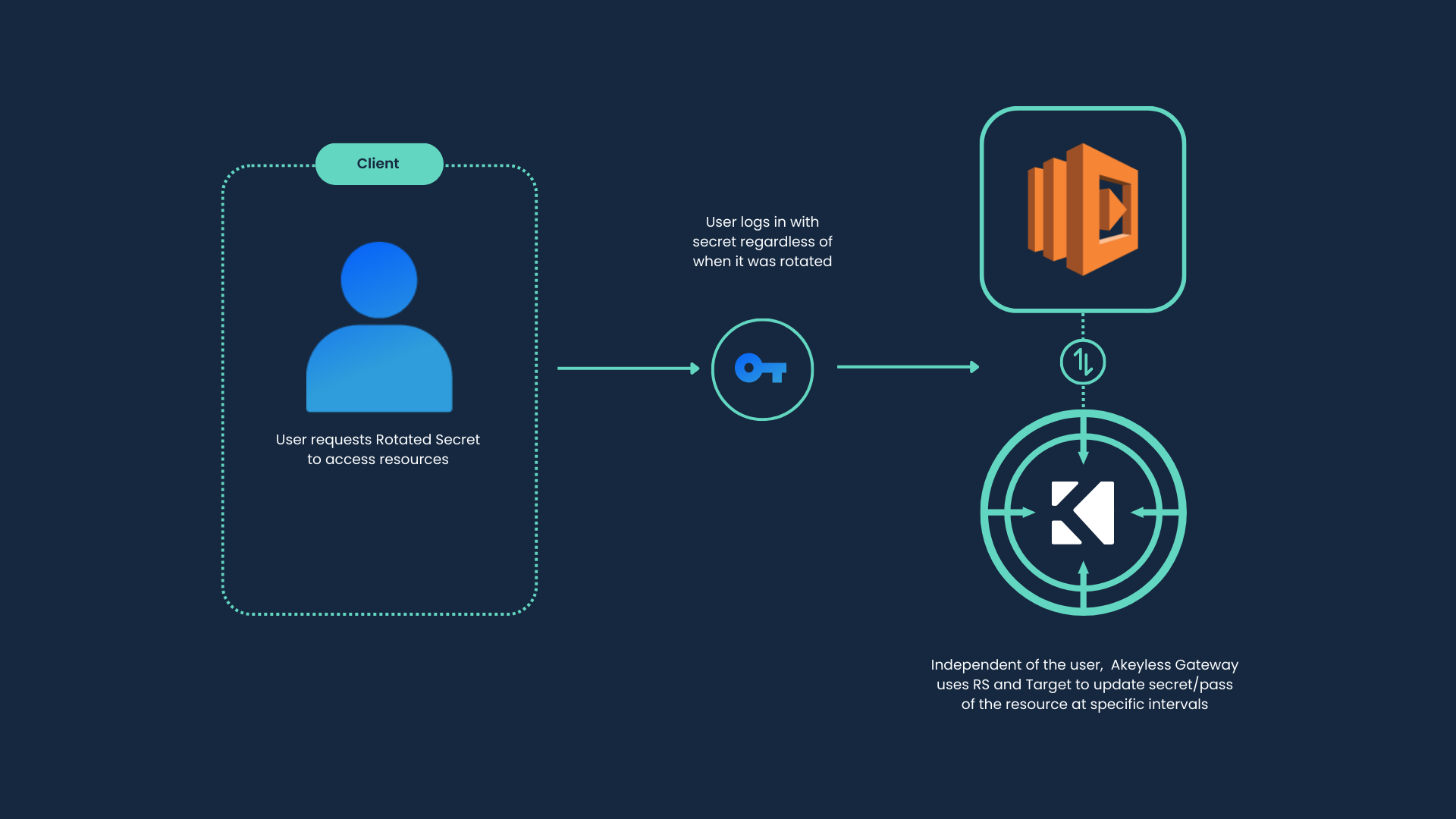
The Akeyless Platform generates a new password, resets it on the target machine, and stores the updated secret value so that it can be retrieved when required.
You can define a rotated secret to automatically update the password at defined intervals, or manually trigger a password update with the CLI or from the Akeyless Console. You also have the ability to set a custom password length for each individual rotated secret.
You can configure:
- AWS Rotated Secret
- Azure Rotated Secret
- Database Rotated Secret
- Docker Hub Rotated Secret
- GCP Rotated Secret
- LDAP Rotated Secret
- Linked Target Rotated Secret
- Splunk Rotated Secret
- SSH Rotated Secret
- Windows Rotated Secret
- Custom Rotated Secret
The typical flow for working with Rotated Secrets is:
-
Create a Target for a Rotated Secret: Get started by defining the target. The rotated secret itself is a user account on the target, for which the password needs to be rotated every
Xdays. -
Create an SSH Rotated Secret or Create an AWS Rotated Secret: When you create a rotated secret, you need to name it and define the secret settings, such as how often the secret should be rotated, and the secret target. All secret values are encrypted using patented Akeyless Distributed Fragment Cryptography (DFC) technology.
-
Add a Rotated Secret to a Role: Enable clients to access the rotated secret by adding it to a role, with the appropriate permissions.
-
Retrieve a Rotated Secret Value: Get the value of a rotated secret when you need it.
If required, you can manually rotate a secret. When a rotated secret becomes obsolete, you can delete it.
Tutorial
Check out our tutorial video on Creating and Using Rotated Secrets.
Updated 21 days ago
