Azure AD - OIDC
To use Azure Active Directory (AAD) as an IdP to authenticate the Akeyless Platform by way of OIDC, follow the steps below.
Create an Application
-
In your Azure account, go to App registrations > New registrations.
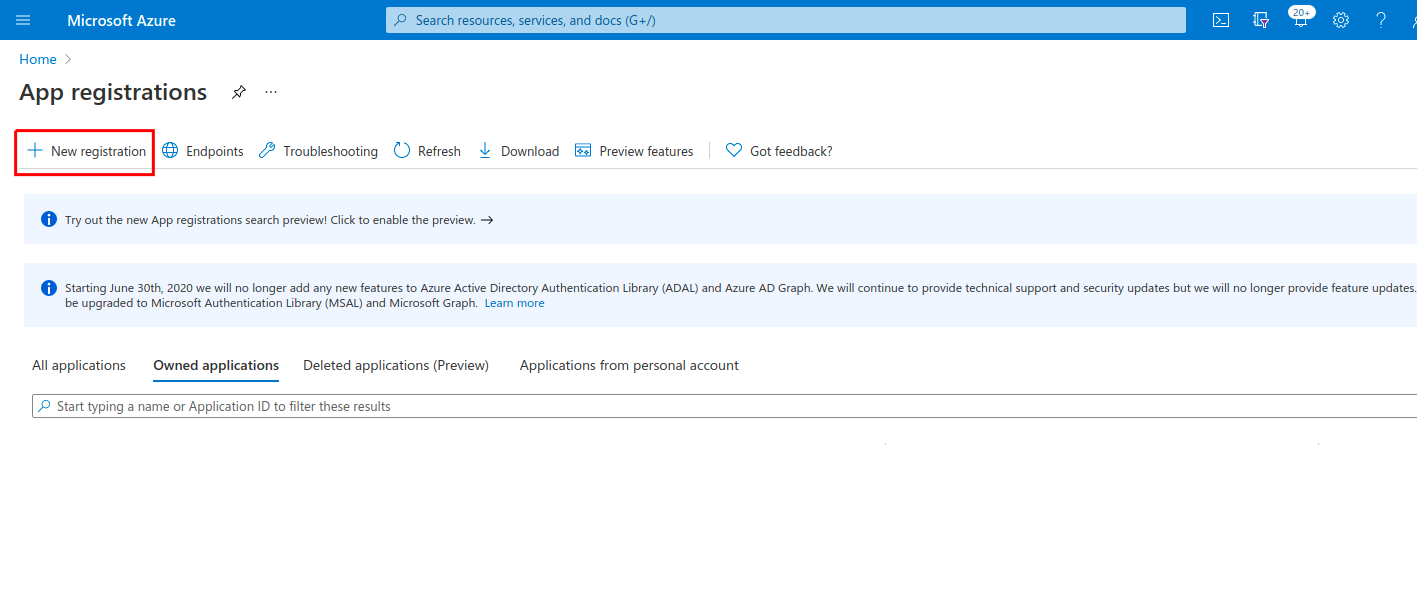
-
For Redirect URI, type select Web for Application type. Set
https://auth.akeyless.io/oidc/callbackas a value and select Register.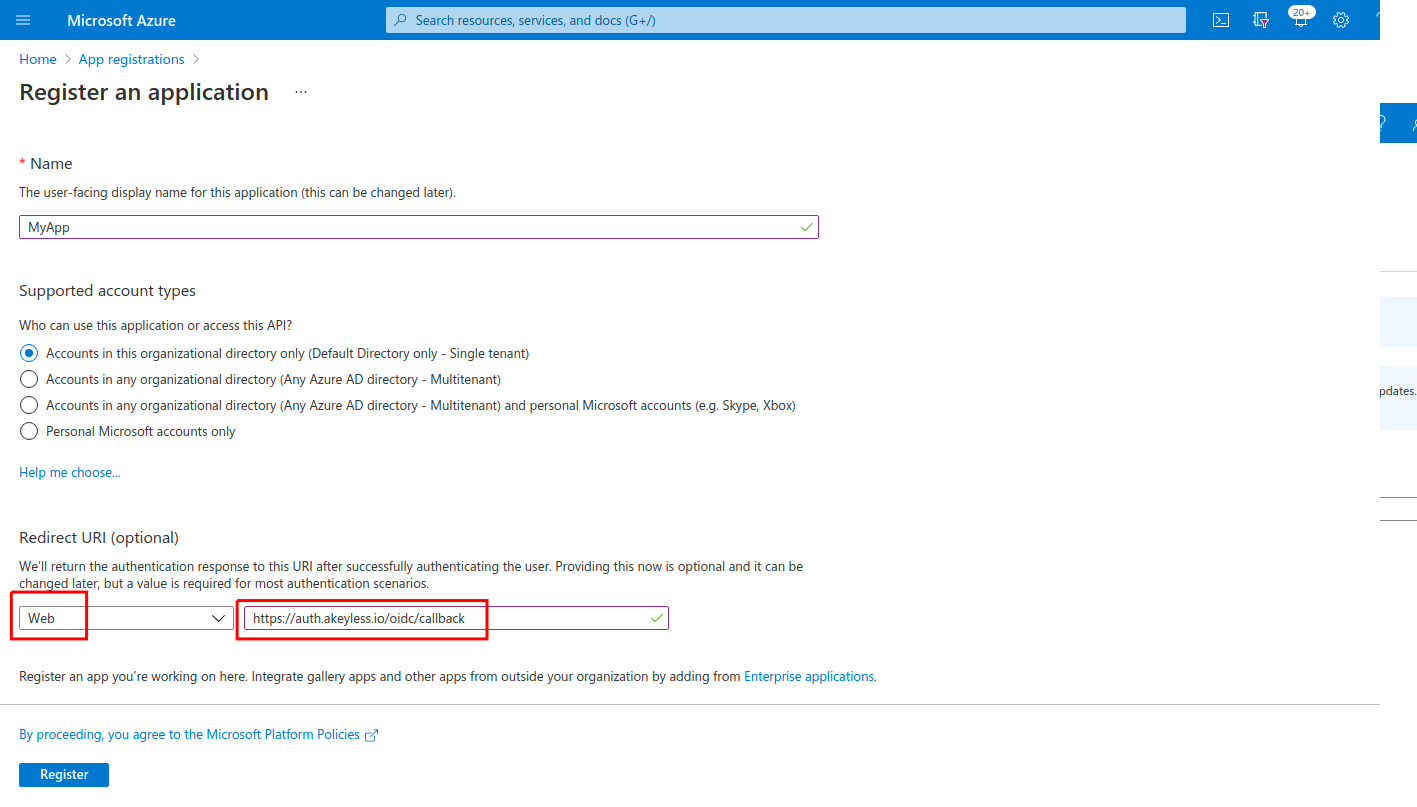
-
Once the app has been created, you need to obtain the Client ID, Client Secret, and the Issuer URL:
- The Client ID can be fetched from Overview > Application (client) ID:
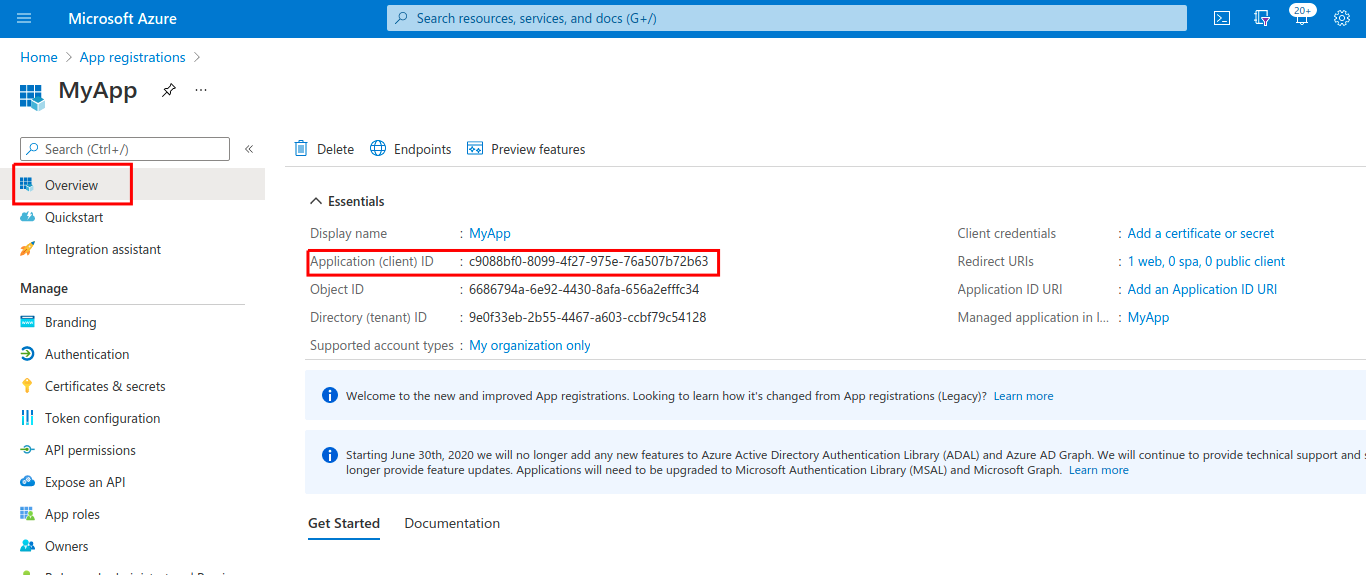
- The Client Secret can be created under Certificates & Secrets > New Client Secret (make sure to copy the Secret Value, not the Secret ID):
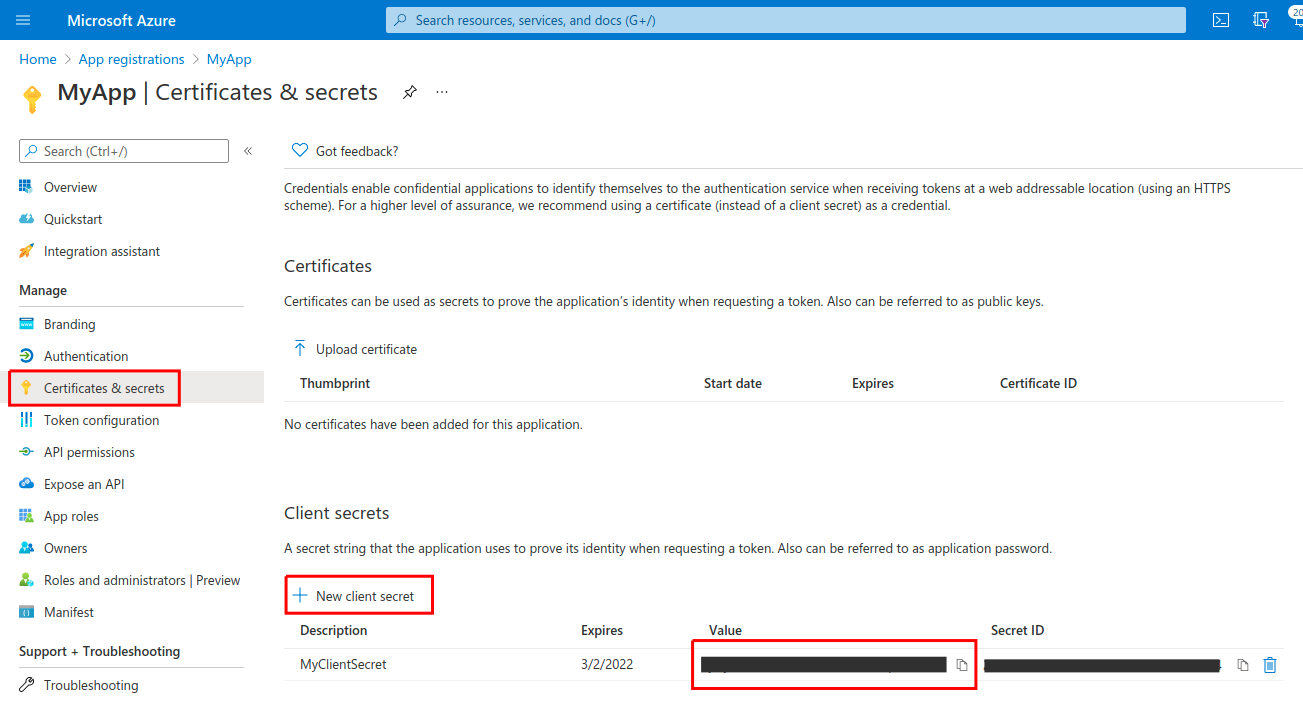
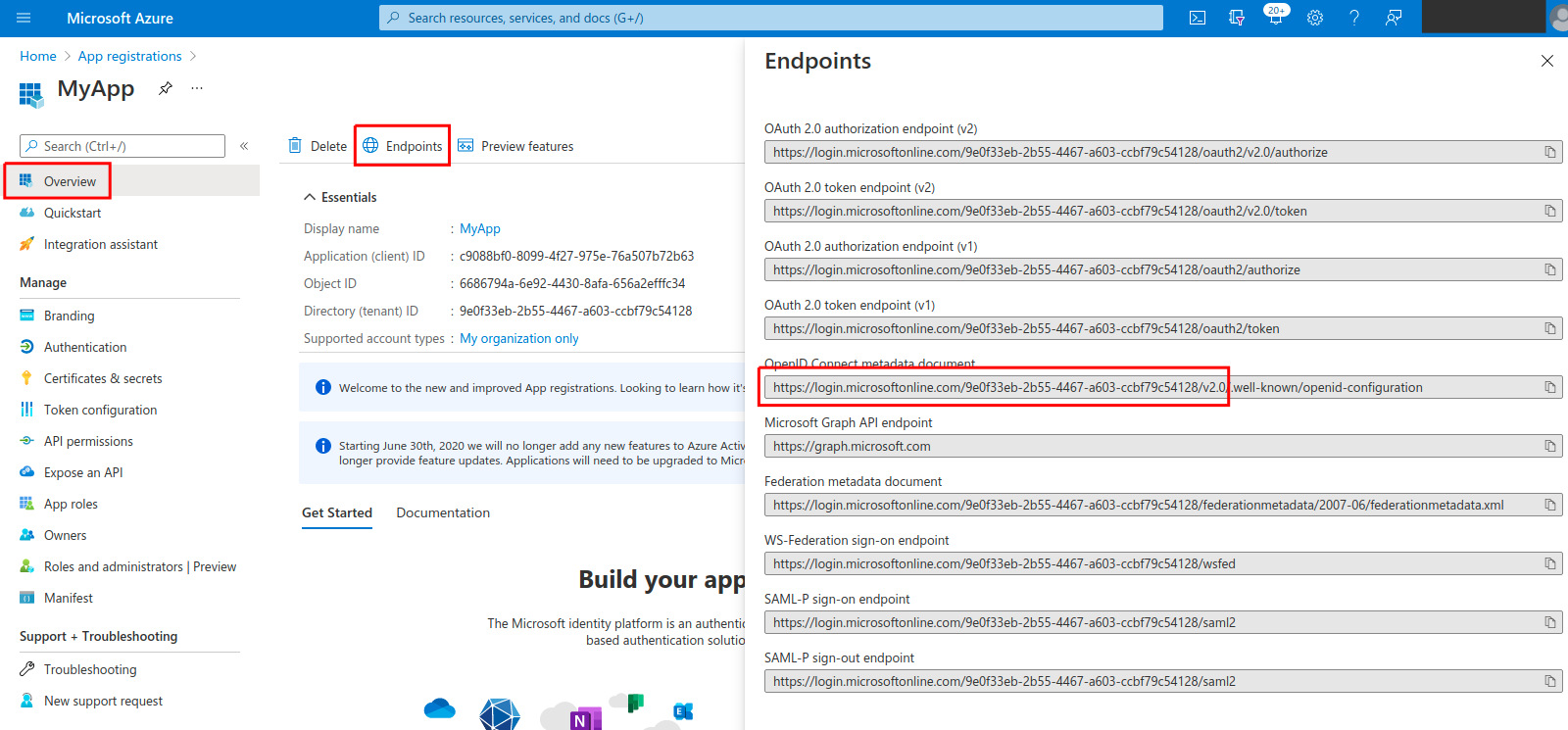
- The Issuer URL can be fetched from Overview > Endpoints > OpenID Connect metadata document (note that the suffix /.well-known/openid-configuration should be omitted so that the Issuer URL will look like:
https://login.microsoftonline.com/tenant-id-abcd-efgh-a123-b456/v2.0):
-
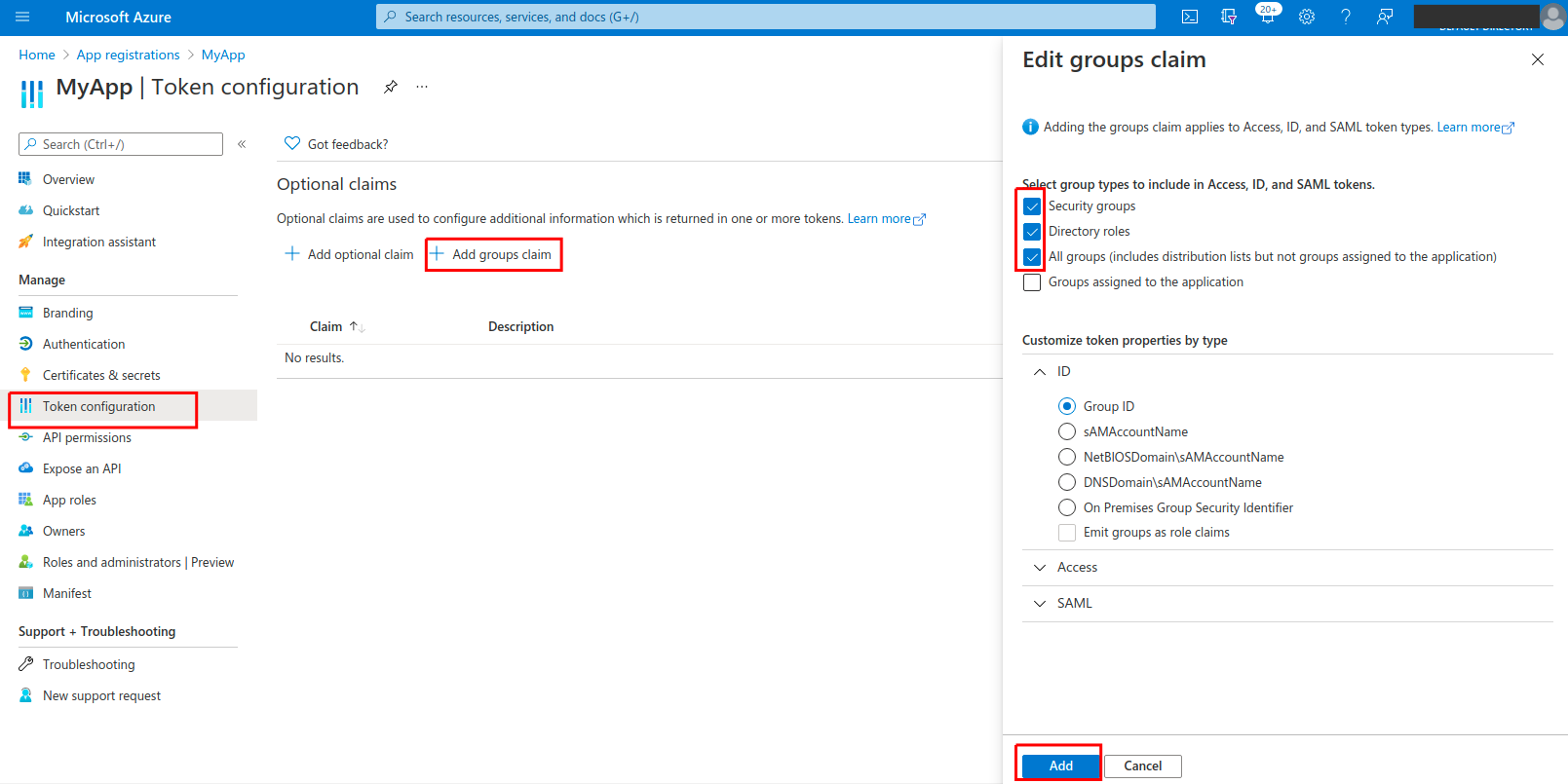
In order to add the AD group as a sub-claim, go to Token configuration > Add Groups Claim:
-
In order to bind the Azure application with your Akeyless account, you need to create an OIDC Authentication Method using either CLI or UI, as described below.
Create an OIDC Authentication Method with the CLI
akeyless auth-method create oidc --name 'my Azure app' --issuer https://{your-issuer-url} --client-id {your-client-id} --client-secret {your-client-secret} --unique-identifier {your-unique-identifier (For example, 'email' or 'username'')}This can also be done from the Console UI by creating a New OIDC Auth Method and filling in the same required parameters.
Notice the unique-identifier must be an available claim, which out of the box might be the "preferred_username" field. If you wish to use a field such as email instead, make sure to first Add optional claim under Token configuration (in the Azure App), and add the email claim.
To log in with SSO to Akeyless with your new Azure AD OIDC Auth Method, login to the Console, browse to Auth Methods, select the newly created OIDC Auth Method, and hit the "Generate OIDC Bookmark URL" - this will provide you with the SSO link.
Login With OIDC with the CLI
You should configure a new profile with your Access-ID from the previous step and OIDC type (if no profile name is provided the default will be configured):
akeyless configure --access-id <your access ID > --access-type oidc --profile 'azure-app'Now, you can run any Akeyless CLI command and be authenticated with the Azure application:
akeyless list-items --profile azure-appUpdated 5 days ago
