Analytics
Akeyless Platform provides rich analytics functionality, allowing the user to analyze the status of his secret posture in various environments with a high-level view.
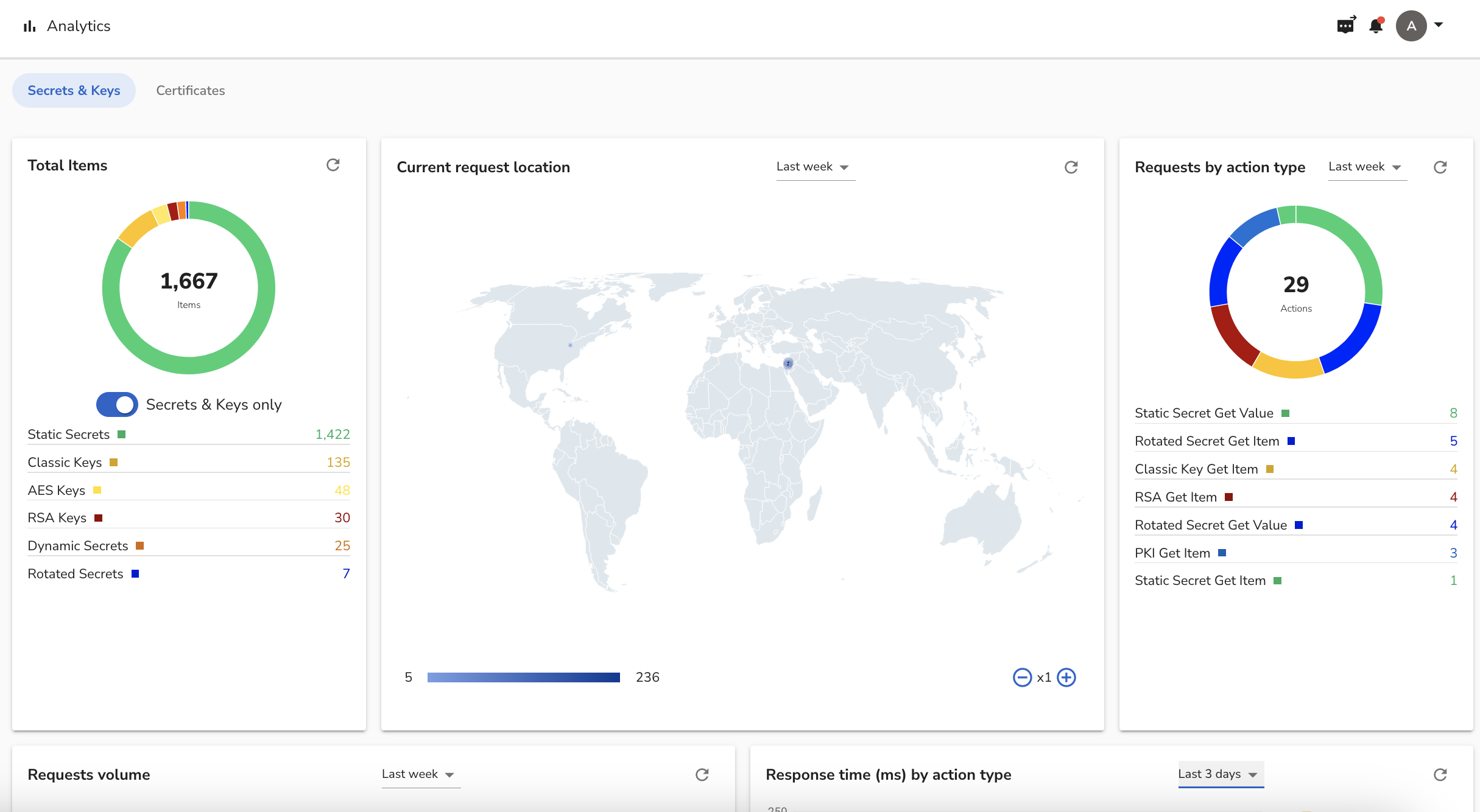
The main screen tab provides information about items, such as Secrets and Keys where the screen is divided into the following parts:
- A geographic map presenting the IP addresses that consume secrets
- Pie chart that represents the division of the requests by the action type, and below the exact number of operations
- Request volume in the allocated timeframe
- Request time by action type (latency)
The user can change the timeframe for which the data is presented.
Navigate to the Certificates tab to get an immediate overview of your certificate's status with additional details on future expiration.
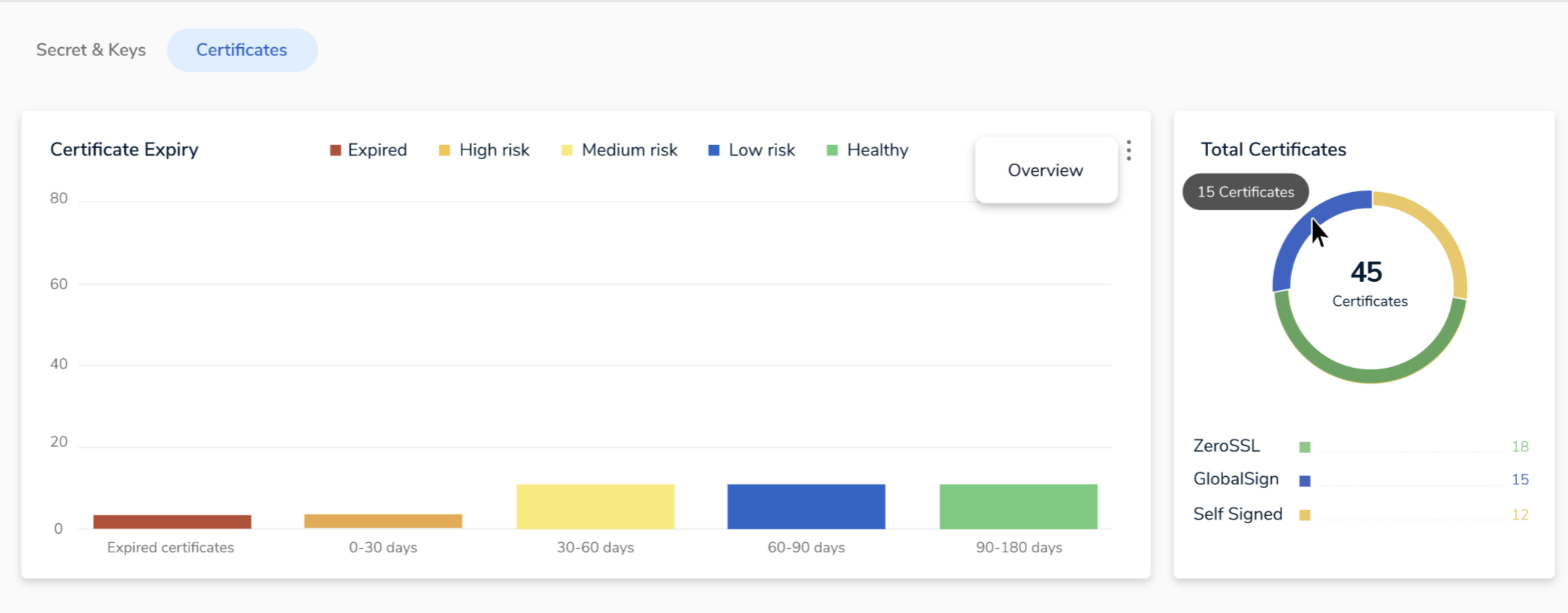
On the Certificate Expiry graph, click on the Overview button in the top right corner to get a detailed overview of all your certificate and their expiration details.
To get the Analytic data using a CLI command run the following command:
akeyless get-analytics-data
Note: Data in the Analytics report includes items stored in Personal Folders.
Tutorial
Check out our tutorial video on Audit Logs, Analytics, and Usage Reports.
Updated about 18 hours ago
