Overview
What Is Secure Remote Access?
The Akeyless Platform’s Secure Remote Access (SRA) solution offers a modern approach to Privileged Access Management (PAM), enabling users to securely connect to servers, databases, internal applications, and web apps across any environment—whether cloud hosted or on-premise, private or public—by leveraging Just-in-Time, Zero-Trust access with full auditability.
Users can connect securely to resources through the Gateway's internal SRA Portal, the public SRA Portal, a desktop application, or by way of the Akeyless Connect CLI command. Akeyless supports a variety of protocols, including SSH, RDP, SQL, kubectl, and more.
Architecture
SRA is deployed alongside the Akeyless Gateway and consists of a Web application and SSH application, each a separate container in the cluster. These applications are deployed on your environment and enable an extra layer of protection between your private network and the cloud:
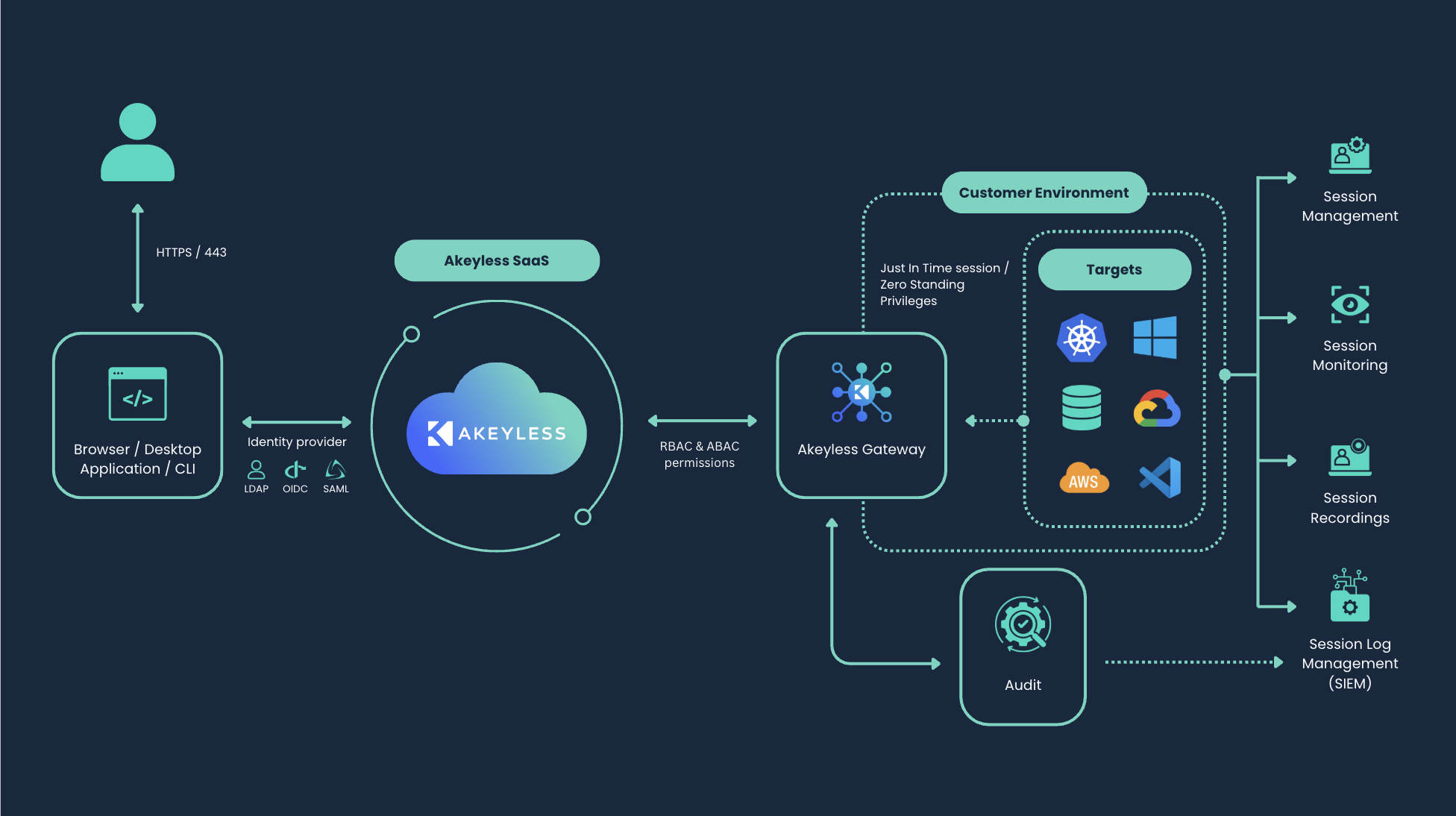
- Web: The web application allows users to securely access internal resources on a browser-based interface by way of the SRA Portal, leveraging embedded clients.
- SSH: The SSH application is primarily used for native CLI access from the users' terminal using the Akeyless Connect and Akeyless SCP commands to any Unix-supporting resource.
To connect to a resource, the user first authenticates to Akeyless by way of a configured Identity Provider (IdP). Once authorized, SRA facilitates the connection in a Zero-Trust manner by retrieving the required secret credentials by way of the Gateway and automatically injecting them into the target resource to establish and proxy the user’s access.
As a result, Akeyless uniquely combines the ability to interface with 3rd-party identity providers for authentication with granular Role-Based Access Control (RBAC) for authorization and the ability to provide Just-in-Time Access to remote resources, using Dynamic Secrets as short-lived credentials and certificates.
Key Features
Akeyless Secure Remote Access provides a robust set of features designed to support secure, efficient access for teams. Here are some of the key capabilities:
- Just-in-Time Access: With SRA, just-in-time secrets can be created and injected into a remote resource, such as a database, on the fly.
- Rotated Secret Access: Privileged secrets can be used to access remote resources with the ability to automatically rotate the credentials once the session ends.
- Support for Various Protocols: Akeyless supports a variety of protocols, including SSH, RDP, SQL, kubectl, and more.
- Request for Access: Admins have the ability to enable an option for users to request access for a specific resource on-demand.
- Audit and Session Management: Akeyless provides full session management with auditing and recording capabilities to keep you compliant. Session recordings and transcripts can be automatically exported to remote storage systems for long-term retention.
- Granular RBAC: Access can be tightly scoped so that each user is granted only the necessary permissions to the specific targets or resources they need (Users are restricted from accessing anything beyond their defined scope). Users only need SRA permissions to initiate connections—without requiring any Read access to the underlying secrets.
- Native SSO integrations: SRA supports authentication by way of SSO protocols such as OIDC, SAML, and LDAP.
- Multiple connection interfaces: WebUI, CLI, Desktop app
Use Cases
Secretless User Access
Allow your users to access sensitive infrastructure resources without credentials.
Just-in-Time Zero-Trust Access
Implement a gold-standard Zero-Trust environment and make auditing a breeze.
Third Party Access
Provide third-party access to resources without compromising your security.
Manage Access to Kubernetes Clusters
Remote Access supports access to any flavor of Kubernetes cluster, including EKS, GKE or any other generic Kubernetes cluster.
Supported Resource Types
Akeyless' Remote Access solution supports connections to the following resource types:
- Databases
- Windows Remote Desktop
- AWS Console
- Azure Portal
- GCP Portal
- SSH Servers
- LDAP Servers
- RabbitMQ
- Kubernetes
- Web Applications
- kubectl
Web Access
In addition, you can define Remote Access to external SaaS systems using the Web Access Application as a separate deployment, not connected to the Gateway. This enables you to remotely access web-based applications in Isolated mode, which restricts user access to only the websites you determine, either while connected to a SaaS system or using a secure proxy mode to enable access for an internal resource from the external network.
For details about the various Remote Access components, see Overview Section.
Updated 10 days ago
