Universal Secrets Connector
While Akeyless is built to store, manage, and protect your secrets internally, it can also be used to manage secrets stored in other secret management services such as AWS, GCP, Azure, or Kubernetes. This can be done seamlessly by creating a Universal Secrets Connector (USC) that uses Targets to establish secure logical access to the related services, enabling indirect management of those secrets. Each USC item derives its permissions from the identity linked to its Target.
When a user is granted read access to a USC item, they can act using the permissions of that underlying identity. With USC, you can unify governance and visibility across fragmented secret stores without migrating data or altering existing workflows.
Universal Secret Connector is also supported by the Akeyless Kubernetes Injector, allowing Kubernetes applications and workloads to access secrets and credentials sourced through USC securely.
After connecting to your Universal Secrets source, you can manage them from Akeyless, including viewing, adding, updating, deleting, and syncing secrets. The exact secret information that can be displayed in Akeyless varies between providers according to their unique attributes.
The USC solution operates in a governance loop model. It automatically detects and reflects changes to your secrets, whether those changes are made in Akeyless or in the remote secret management system. Akeyless does not store a copy of external secrets; therefore, data residency and security policies remain unchanged. The USC reflects updates in real time and does not require any configuration changes on the remote secret management endpoint.
Setting up Universal Secret Connector requires the Defaults permission on the Gateway.
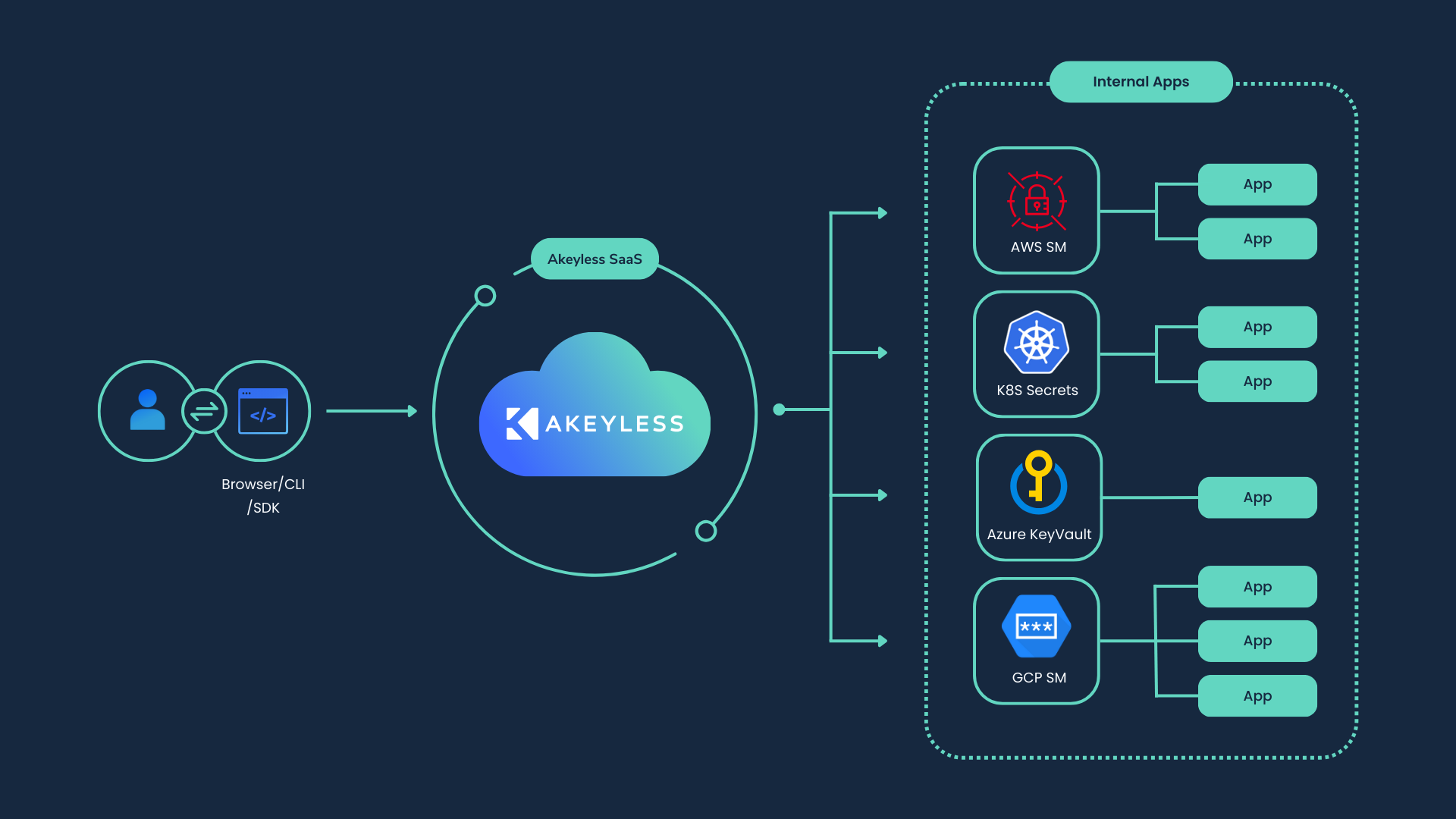
Akeyless currently supports creating Universal Secrets Connectors for the following services:
To view all your Universal Secret Connectors, log in to the Console then navigate to Items > Universal Secrets Connector.
Tutorial
Check out our tutorial video on Universal Secrets Connectors.
Updated 10 days ago
