AWS IAM
AWS Identity and Access Management (IAM)
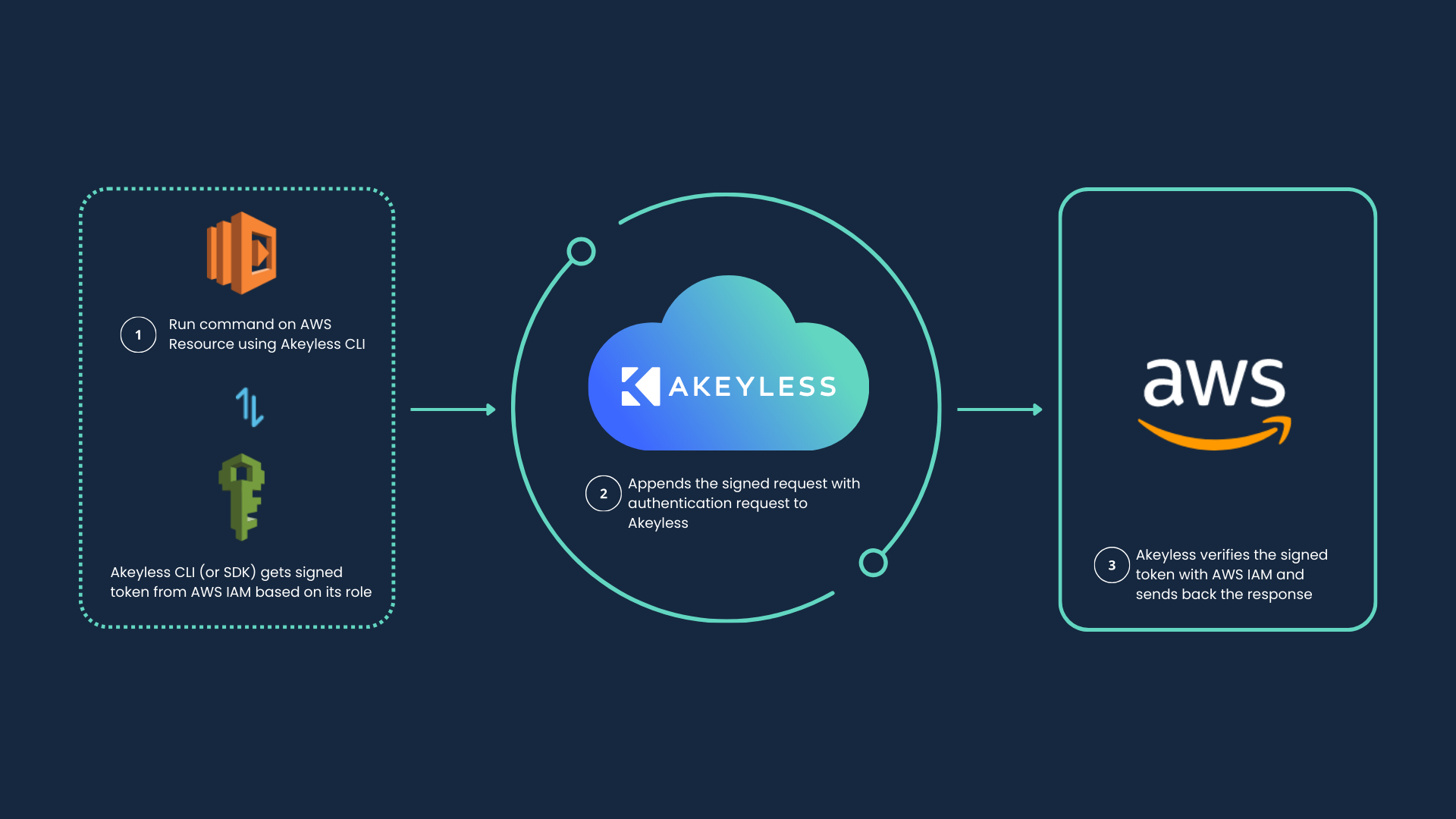
AWS IAM authentication method provides an automated flow to retrieve an Akeyless token for IAM principals and AWS services or resources.
Create an AWS IAM Authentication Method with the CLI
Let's create a new AWS IAM authentication method using the Akeyless CLI. (You can do this also from the Akeyless Console.)
To create an AWS IAM authentication method with the CLI, run the following command:
akeyless auth-method create aws-iam \
--name <Auth Method Name> \
--bound-aws-account-id <AWS Account ID>Where:
-
name: A unique name for the authentication method. The name can include the path to the virtual folder where you want to create the new authentication method, using slash/separators. If the folder does not exist, it will be created together with the authentication method. -
bound-aws-account-id: An AWS account ID that is allowed to authenticate to Akeyless using this authentication method. (You can provide more than one AWS account ID by using this parameter in the following format:--bound-aws-account-id AWS-ID-1 --bound-aws-account-id AWS-ID-2.)
You can find the complete list of additional parameters for this command in the CLI Reference - Authentication section.
Configure Akeyless CLI With the AWS IAM Authentication Method
To configure your CLI to work with AWS IAM authentication, run the following command from an AWS resource:
akeyless configure --profile default --access-id <AccessID> --access-type aws_iam
akeyless get-cloud-identity --cloud-provider aws_iam
Least Privileged PermissionsAWS IAM authentication doesn't require any privileged permissions. Ensure you have an IAM role without any privileged permissions and attach it to the resource you want to authenticate (For example, EC2 instance).
Create an AWS IAM Authentication Method in the Akeyless Console
-
Log in to the Akeyless Console and go to Users & Auth Methods > New > AWS IAM.
-
Define a Name for the authentication method, and specify the Location as a path to the virtual folder where you want to create the new authentication method, using slash
/separators. If the folder does not exist, it will be created together with the authentication method. -
Define the remaining parameters as follows:
-
Expiration Date: Select the access expiration date. This parameter is optional. Leave it empty for access to continue without an expiration date.
-
Allowed Client IPs: Enter a comma-separated list of CIDR blocks from which the client can issue calls to the proxy. By "client," we mean CURL, SDK, and so on. This parameter is optional. Leave it empty for unrestricted access.
-
Allowed Trusted Gateway IPs: Comma separated CIDR blocks. If specified, the Gateway using this IP range will be trusted to forward the original client IP. If empty, the Gateway's IP address will be used.
-
Audit Log Sub Claims: Enter a comma-separated list of sub-claims keys to be included in the Audit Logs.
-
Allowed Client Type: Select the allowed client type that will be authorized to use this authentication method. For example,
CLI,SDK,Gateway Admin. -
Bounded AWS Account IDs: Enter a comma-separated list of AWS account IDs for which access is allowed.
-
Bounded ARNs: Enter a comma-separated list of full IAM role ARNs for which access is allowed. For example:
arn:aws:sts:{account-id}:assumed-role/{role-name}/{resource-id}, arn:aws:iam::{account-id}:user/{user-name}. Or use wildcard characters like*or?to grant multiple roles within a single ARN Role. For example,arn:aws:sts:us-east-?:123456789012:*would allow any IAM role in the AWS account to login tous-eastregions. This parameter is optional. Leave it empty for unrestricted access. -
Bounded Role Names: Enter a comma-separated list of AWS role names for which access is allowed. This parameter is optional. Leave it empty for unrestricted access.
-
Bounded Role IDs: Enter a comma-separated list of AWS role IDs for which access is allowed. This parameter is optional. Leave it empty for unrestricted access.
-
Bounded User names: Enter a comma-separated list of usernames for which access is allowed. This parameter is optional. Leave it empty for unrestricted access.
-
Custom STS Endpoint: Default value is
https://sts.amazonaws.com. -
Unique Identifier: Optional, a unique identifier (ID) value that contains details uniquely identifying that resource. This sub-claim name is used to distinguish between different identities.
-
-
Click Finish.
AWS Instance Metadata Service
By default, Instance Metadata Service (IMDSv2) enforces a hop limit of 1, which means the metadata token used for cloud identity (such as IAM role credentials) must be accessed directly from the EC2 instance that initiated the session.
If the Akeyless Gateway runs in a different network context (For example, inside a container), it may fail to authenticate using the aws_iam authentication method because this hop limitation.
To resolve this, you can increase the allowed number of network hops by modifying the http-put-response-hop-limit parameter. This can be done by way of the AWS CLI or the AWS Management Console.
The following command increases Hop Limit to 2:
aws ec2 modify-instance-metadata-options \
--instance-id <instance-id> \
--http-put-response-hop-limit 2This allows the metadata token to be accessed from within nested network environments, such as containers, while still maintaining IMDSv2's security benefits.
Tutorial
Check out our tutorial video on AWS IAM Authentication and Access.
Updated 16 days ago
Make sure to associate your new Authentication Method with an Access Role to grant the relevant permissions within Akeyless
