Dynamic Secrets
Dynamic Secrets are secrets that are generated every time they are accessed, using permissions you've defined in advance. In this way, users can access a resource for a temporary period with a defined set of permissions. You can configure multiple Dynamic Secrets for the same resource to granularly control the breadth of access either per a temporary user on a specific target or for the entire target within a single action. You can revoke all temporary users immediately for a specific target as necessary.
Setting up Dynamic Secrets requires the Dynamic Secret permission on the Gateway.
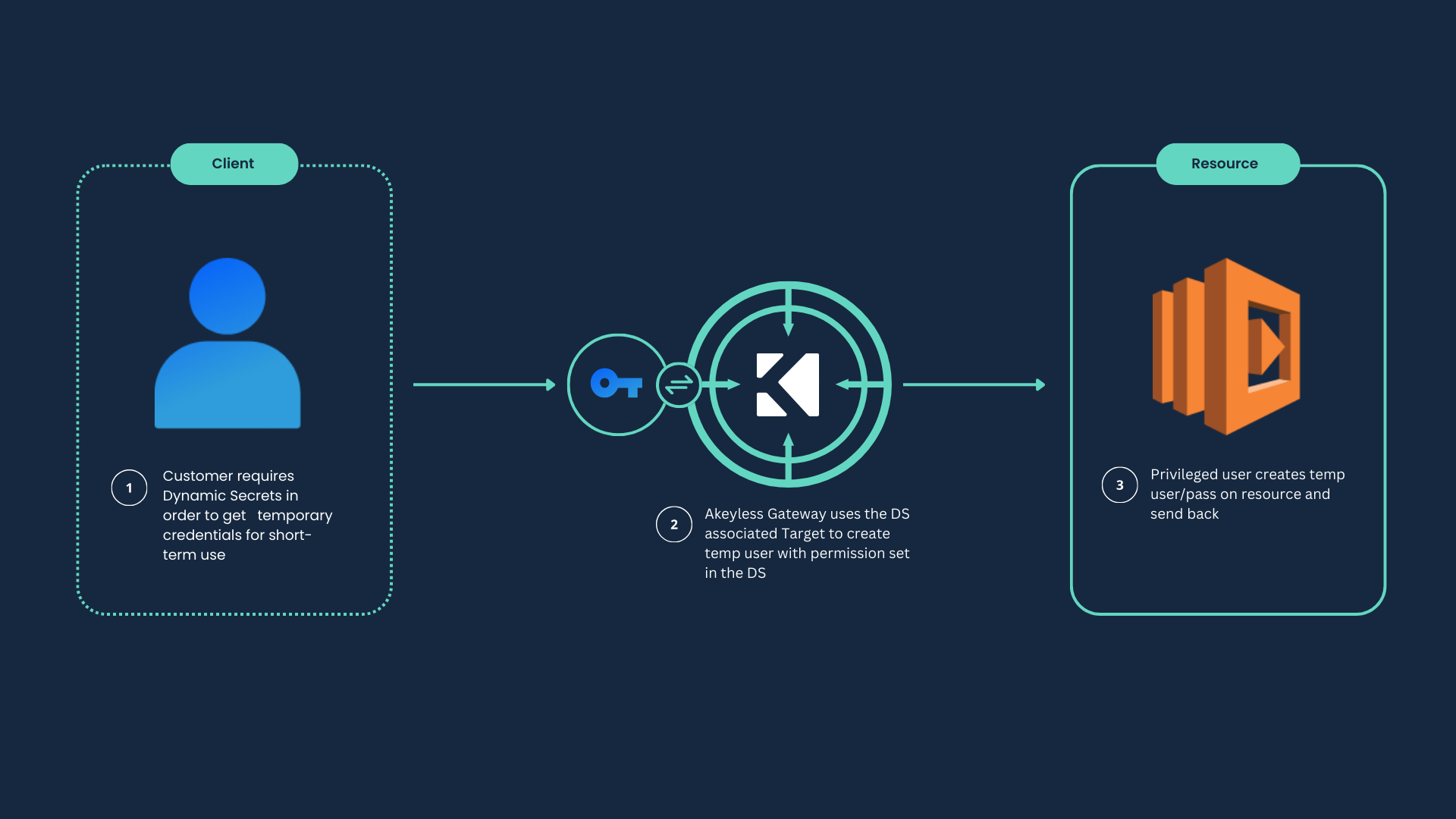
To create a dynamic secret, you must configure the required account and access credentials. The Akeyless Platform uses these to communicate with the resource and get short-lived passwords as required. You can configure:
- Database Dynamic Secrets
- Artifactory Dynamic Secrets
- AWS Dynamic Secrets
- Azure AD Dynamic Secrets
- GCP Dynamic Secrets
- EKS Dynamic Secrets
- GKE Dynamic Secrets
- LDAP Dynamic Secret
- RabbitMQ Dynamic Secrets
- Snowflake Dynamic Secrets
- RDP Dynamic Secrets
- GitHub Dynamic Secret
- OpenAI Dynamic Secret
- GitLab Dynamic Secret
- Docker Hub Dynamic Secrets
- Kubernetes Generic Dynamic Secrets
- Chef Infra Dynamic Secrets
- Ping Dynamic Secrets
- Custom Dynamic Secrets
Info:The configuration required to produce Dynamic Secrets is part of your private network, and are stored on the Akeyless Gateway.
Get the value of a dynamic secret when you need it.
Tutorial
Check out our tutorial video on Creating and Using Dynamic Secrets.
Updated 3 days ago
